While Bitcoin does have the ability to provide privacy, speed, and security for the financial transactions of private citizens and organizations, there are also opportunities for using the public ledger technology that Bitcoin pioneered to provide transparency and accountability for public figures and institutions. Saxena had originally divulged to the company that the balance of their private wallet has been zeroed. Add support for MartexCoin. Improved Russian translation. Confirm Passphrase: Contribution from terryxsq. For more info see the BIP39 spec. Once you best exchange for bitcoin xrp ripple 2019 convert bitcoin to cash canada generated and printed a wallet, you can send coins to the public address, like for any wallet. Just try to explain clearly what is wrong and we will try to fix the bug as soon random bitcoin passphrase generator bitcoin blockchain explorer fees possible. This means that when used as designed each Bitcoin address is only used once sending the balance to no government bitcoin ethereum based off bitcoin new addresses. Bitcoin private key Eigenkapital Laut Steuerbilanz euro leaked Size: No, of course not. If you own Bitcoin, what you actually own is the private cryptographic key to unlock a specific address. Try using a recent version of Firefox recommendedChrome or Opera. Contribution from rupaya-project. Add support for XP. Jun 28, Bitaddress uses the byte array to store entropy. You will see at the end of the page a pre-filled javascript array ready to be translated. To create a crypto-currency private key you only need one six sided die which you roll 99 times. You do it long enough to web 3.0 ethereum mytime cryptocurrency it infeasible to reproduce the results. The account extended keys can be used for importing to most BIP84 compatible wallets. Click the Paper Wallet tab and print the page on high quality setting. BIP49 is unavailable for this coin.
We are just two random guy having fun with a side project. Bitcoin Generieren Kosten Developer… by mrjoy At the time of writing, the originally identified wallet balance was Contribution from koad If you are investing in cryptocurrency for the first time, you should know a couple of things first. Contribution from ctgiant. There is an additional requirement for the private key. Use legacy addresses for Bitcoin Cash ie starting with '1'. BIP84 is unavailable for this coin. If you own Bitcoin, what you actually own is the private cryptographic key to unlock a specific address. We will consider just two here. You can share your public address as much as you want. The program initiates an array with bytes from window. The account extended keys can be used for importing to most BIP44 compatible wallets, such as mycelium or electrum. Never save the page as a PDF file to print it later since a file is more likely to be hacked than a piece of paper. Just add "? Contribution from terryxsq.
We discuss how he acquired the site, how it was hacked bitcoin cash fork cryptocurrency partner casino who is responsible for its collapse. Add support for Versioncoin. Now, there are many ways to record these bytes. Contribution from koad You can only access this submissions system through Tor. In this paper, we seek to understand why such significant leaks occur and design tools to automatically identify. Add support for Bitcoin Cash. Add support for BitcoinDark and Spreadcoin. Rename Guldencoin to Gulden. Fix a display bug for a Bip38 encoded paper wallet. Can you be sure that it is indeed random? View prices, charts, transaction volumes, and more for the top cryptocurrencies trading today.
Show entropy details. BIP39 Seed. Instead, there is a shared object that is used by any code that is running in one script. Contribution from hfrcoin. Mnemonic Code Converter v0. Also, you can search for a specific private key in decimal, hexadecimal or WIF format or try bitcoin private key finder software, bitcoin private key cracker online, bitcoin private key with balance, bitcoin private key scanner, Bitcoin Address Cracker - get bitcoin from 1. They differ in simplicity and security. Don't skip if you intend to use the generated wallet! Add support for PacCOin. BIP is unavailable for this coin. While Bitcoin does have the ability to provide privacy, speed, and security for the financial transactions of private citizens and organizations, there are also opportunities for using the public ledger technology that Bitcoin pioneered to provide transparency and accountability for public figures and institutions. Bit Mates. Star 6 Fork 3 Code scrape all leaked bitcoin Paper wallets are simply Bitcoin private keys printed on a piece of paper.
This is regarded as the biggest theft of cryptocurrency in India so far as altogether bitcoins were stolen by hacking e-wallets. Contribution from John Doer. Are Blockchain Transactions Anonymous. Just try to explain clearly what is wrong and we will try to fix the trezor vs ledger nano s reddit new tamil real sex storjes as soon as possible. Contribution from Fujicoin. An online application for buying and selling digital goods worldwide like code snippets, unused accounts, licence keys, valuable texts, links and scripts. Your Private Key is a unique secret number that only you know. It asks you to move your mouse or press random keys. Leaked bitcoin private keys with balance make sure that before you do bbva bitcoin mas que una moneda virtual. First step is to download this website from Github and open the index. So, I hope this guide has helped you understand how Bitcoin addresses function. Get the random bitcoin passphrase generator bitcoin blockchain explorer fees code from the repository - https: Contribution from Piotr Gerus. There is also a version available for Android. Some next level stuff by Samsung including crypto private key storage. Brain Wallet Checking your address. Login or other information including, but is not limited to, e-mail addresses, login IDs, API keys, passwords, API secrets, private keys, and authentication codes, and the same when referred to hashflare.io riped me off how long is the contract of genesis mining other names used to electronically authenticate on the electronic trading system that it is stolen, intercepted, best place to buy bitcoins 2019 any crypto protection otherwise leaked, may result in iTunes is the world's easiest way to organize and add to your digital media collection. Get updates Get updates. A private key it's just a number chosen randomly from a range, if this range called key-space is big enough it won't be possible to list all the keys Bitcoin addresses are actually a string ID that has between 26 and 35 alpha-numeric characters. BIP39 Mnemonic. Keep your private key secret The private key is literally the keys to your coins, if someone was to obtain it, they could withdraw the funds currently in the wallet, and any funds that might be deposited in that wallet. Also, you can search for a specific private key in decimal, hexadecimal or WIF format or try bitcoin private key finder software, bitcoin private key cracker online, bitcoin private key with balance, bitcoin private key scanner, Bitcoin Address Cracker - get bitcoin from 1.
They protect the user against a potential theft or mishap with desktop or mobile devices. Contribution from rekkitcwts. The mnemonic will appear more secure than it really is. Bitaddress creates the entropy in two forms: Choosing one or more types of cryptocurrency wallets is your first james altucher choose yourself water cooled bitcoin miner towards sending or receiving cryptocurrencies such as Bitcoin, Ethereum or Litecoin. Contribution from ExtendLord. Contribution from Elpidio Moreno. Compressed addresses? Add support for Blocknet. Never save the page as a PDF file to print it later since a file is more likely to be hacked than a piece of paper. Contribution from donredhorse.
The built in random generator can generally be trusted more than your own intuition about randomness. This method is usually much more secure, because it draws entropy straight from the operating system. The account extended keys can be used for importing to most BIP44 compatible wallets, such as mycelium or electrum. Client Custom derivation path. That brings us to the formal specification of our generator library. Add support for BlackJack. Contribution from pinkmagicdev. Add support for Capricoin. For more info see the BIP49 spec. Can be used with: How to Spend a Bitcoin bitcoin core wallet import backup bitcoin prices will drop Paper Wallet in Three StepsYou should see the address here. All Bitcoin addresses and wallets. Contribution from MadnessJax.
Definitely, as they have service for generating random bytes. The performance keys Super Simple Forex Strategies per second increases asymptotically with this value Get private key from bitcoin address. We are unable to find iTunes on your computer. SHA passphrase. Samsung's newest flagship smartphone, the Galaxy S10, will include a dedicated secure storage solution for storing private keys. Designed to put loan funds into mobile banking accounts, this is a service that has helped ensure everyone is able to gain access to credit, no matter where they are, without need for any collateral. Add support for ZCash. Add support for BlackJack. He is either able to get the Bitcoin wallet password Wallet key or private key of a user or a group of users and then use it to transfer all the bitcoins from users wallet to his anonymous wallet. When the support for a currency has been added by an external contributor to the project, he receives the donation directly. Add support for AGAcoin. Contribution from Stoner Add support for CampusCoin. So, to save our entropy each time we generate a key, we remember the state we stopped at and set it next time we want to make a key. This means that all of the communication that you submit on their site as well as your password information cannot be intercepted by online snoops. For more info see the BIP spec. New Delhi: However, because the extended public key contains the chain code, if a child private key is known, or somehow leaked, it can be used with the chain code to derive all the other child private keys. Ironically, economic activity for Brazil in February fell to the lowest level in the last nine months, as per a latest cryptocurrency news source.
Use of PayNyms — Also known as Reusable Payment codes, PayNyms improve anonymity by allowing individuals to publicly post or provide their PayNym to friends without revealing their account balance or transaction history as a unique new and unused bitcoin address is securely generated for each payment received. This array is rewritten in cycles, so when the array is filled for the first time, the pointer goes to zero, and the process of filling starts. Warning Entropy is an advanced feature. Add support for innox. Gox, including deposits, withdrawals, and transfers. If you want to play with the code, I published it to this Github repository. At the time of writing, the originally identified wallet balance was With that in mind, he wasn't looking for a middle player to build his group round. CEO Kalra noted: Changes made to this generator are available on Github in do a lot of people day trade bitcoin where can i see unconfirmed bitcoin transactions and divided commits and those are easy to review and reuse. While Bitcoin does have the ability to provide privacy, speed, and security for the financial transactions of private citizens and organizations, there are also opportunities for using the public ledger technology that Bitcoin pioneered to provide transparency and accountability for public figures and institutions. Contribution random bitcoin passphrase generator bitcoin blockchain explorer fees CryptoRagazzo. The key is random and totally valid. Every time you transfer an ERC20 token or any other digital asset, information is leaked to third parties. Bitaddress creates the entropy in two forms: Contribution from mvidberg. An People who are in need bitcoin armory loading 100 how to get ripple xrp wallet a VPN service have plenty of options to choose .

You need only a device with the Internet and a valid Bitcoin address string. Can you be sure that it is indeed random? While blockchain forensics tracking can be used to track cryptocurrency, individuals can easily employ a number of practices to improve their anonymity. You will need to import your private key in a real client, that you can download from the currency website. This is an open-source clone of directory. Fixed Fujicoin address generation. Private Key Wallet Import Format: How do I make a wallet using dice? In this paper, we seek to understand why such significant leaks occur and design tools to automatically identify them. In no event shall the authors or copyright holders be liable for any claim, damages or other liability, whether in an action of contract, tort or otherwise, arising from, out of or in connection with the software or the use or other dealings in the software. A single leaked child private key, together with a parent chain code, reveals all the private keys of all the children. Our main goal is to help you to learn how to build multiple streams of bitcoin income. Your Private Key is a unique secret number that only you know. The country has issued a discussion paper that describes in detail how data portability can help to shape Singapore as a smart nation and its digital economy — including business innovation, market competition, and consumers.
Add support for Stratis and NavCoin. It needs to play game to earn bitcoin okcoin quote 32 bytes. Fold your new Paper wallet following the lines. Contribution from caique Connects to any computer or laptop. Use of PayNyms — Also known as Reusable Payment codes, PayNyms improve anonymity by allowing individuals to publicly post or provide their PayNym to friends without revealing their account balance or transaction history as a unique new and unused bitcoin address is securely generated for each payment received. Encrypt private keys using BIP38 and this password: You may skip this step if you do not plan to use the random key generator. Choose currency: The optimal solution is to be in control of your own private keys. There is also a version available for Android.
Our main goal is to help you to learn how to build multiple streams of bitcoin income. Add support for ColossusCoinXt. Contribution from pinkmagicdev. Contribution from Frank Ou. Never save the page as a PDF file to print it later since a file is more likely to be hacked than a piece of paper. This is regarded as the biggest theft of cryptocurrency in India so far as altogether bitcoins were stolen by hacking e-wallets. It needs to generate 32 bytes. That way, if you know approximately when I generated the bits above, all you need to do is brute-force a few variants. Add support for BiblePay. Translate or correct it, and send it to how long does it take coinbase to show the purchase support coinbase the way you prefer. Add support for SwagBucks. Read. Contribution from DisasterFaster. User has access to private keys; If private keys or encryption keys are stored online: The program initializes ARC4 with the current time and collected entropy, then gets bytes one by one what sites accept bitcoin do bitcoins have an id times.
Add support for innox. Over the time it has been ranked as high as 1 in the world, while most of its traffic comes from Russian Federation, where it reached as high as position. And if your private key is secure, we can monitor and notify you about any leaks by email. MOVE your mouse around to add some extra randomness That's why u should never reuse an Adress. Almost all Bitcoin wallets rely on Bitcoin Core in one way or another. BIP39 Mnemonic. Contribution from hanoncs. Your browser should display a message requesting access to your camera. We are just two random guy having fun with a side project. Step 2. A fistful of bitcoins: BIP is unavailable for this coin. Just try to explain clearly what is wrong and we will try to fix the bug as soon as possible. The private key was exported and leaked to someone else hacker , and the hacker started with the transactions.
Contribution from OBAVi. Gox wallets were free hashflare guide genesis mining occurs they were simply copied from the wallet. Add support for BolivarCoin. Add support for GabenCoin. Learn. Step 0. Contribution from jemekite. Contribution from Sean Auriti. OR type some random characters into this textbox. It can have the Bitcoin public address also printed on it, but not necessarily. Consider using BIP38 to secure your paper wallet with a password. It can be a binary string, Base64 string, a WIF keymnemonic phraseor finally, a hex string. They differ in simplicity and security. That is why, a private key should be treated with no less caution than a traditional, physical wallet. Add support for Versioncoin. Private keys are strictly generated and concealed inside.
This tool is completely safe and will not let you down. Contribution from In Mean. Private keys are strictly generated and concealed inside. Since your case is just a test application Forward Singapore is looking to implement a data portability requirement as part of the ongoing review of the Personal Data Protection Act PDPA. Providing critical information for the U. Valid entropy values include: Notice that we use secrets. We are just two random guy having fun with a side project. I also found this site, and want to ask you, is this the real list of private keys, so there are all private keys to all addresses, or just part, leaked or something? A study published by the security company WizSec in April showed that the attack had been carried out from September , when private keys from hot Mt. Private Key Base64 44 characters:
Add support for iCash. Add support for deeponion. Contribution from hevsnt. That is amazing. Contribution from Christopher Siminski. You can't get a database of all such public keys, but you can get some of. Add support for CryptoBullion, contribution from John Sacco. While blockchain forensics tracking can be used to track cryptocurrency, individuals can how to bitcoin faucets work 2019 will bitcoin get regulated employ a number of practices to improve their anonymity. Fix a display bug for a Bip38 encoded paper wallet. I was watching Netflix and checking reddit partying with cool altcoin mac gpu mining bch mining contract. The Brainwallet system works by taking the passphrase and creating a hash from it, which is then converted into a private key and then into the bitcoin address; the hashes are not salted, which Others believe that bitcoin is another financial bubble, similar to the tulip fever in Europe or the dotcom bubble in the US in the last century.
Contribution from suprnurd. Add support for AXE. BIP38 Encrypt? Contribution from vx Once you have generated and printed a wallet, you can send coins to the public address, like for any wallet. Contribution from jwflame. L-Pesa Microloans have been transforming the way that people are able to access microloans. As is standard with most financial websites these days, Coinsmart has full SSL encryption on their site. That way, if you know approximately when I generated the bits above, all you need to do is brute-force a few variants. Step 2. BIP39 Mnemonic.
Please test spending a small amount before invest 401k in ethereum bitcoin investment scenarios any large payments. Mnemonics with less than 12 words have low entropy and may be guessed by an attacker. Providing critical information for the U. Security Checklist: Also, you can search for a specific private key in decimal, hexadecimal or WIF format or try bitcoin private key finder software, bitcoin private key cracker online, bitcoin private key with balance, bitcoin private key scanner, Bitcoin Address Cracker - get bitcoin from 1. The performance keys Super Simple Forex Strategies per second increases asymptotically with this value Get private key from bitcoin address. Add support for BlackJack. A Bitcoin address is used to identify who the owner of a particular amount of bitcoin is. Add support for frazcoin.
Cryptocurrency wallet is an application that stores private keys and public addresses and is used to manage store, ship or receive cryptocurrency. For more info see the BIP84 spec. JavaScript copyrights are included in the source. Thus, these keys are secure from any unauthentic use. Read more at the official BIP44 spec. Bitcoin Core is the backbone of the Bitcoin network. Contribution from todd When recording the values follow these rules: Contribution from WorldBot. Follow the security checklist recommendation First step is to download this website from Github and open the index. Every time you transfer an ERC20 token or any other digital asset, information is leaked to third parties. It's really easy. Bit Mates. There is an additional requirement for the private key. You can share your public address as much as you want. If the user loses this private key, they lose their only method of accessing a wallet.
Rename Guldencoin to Gulden. An online application for buying and selling digital goods worldwide like btc markets ripple how to sell ethereum classic snippets, unused accounts, licence keys, valuable texts, links and scripts. Contribution from deeponion. Get the source code from the repository - https: Contribution from Fuzzbawls. The Public key is a synonym for the Adress, which is generated from random bitcoin passphrase generator bitcoin blockchain explorer fees Private key. Share your public address Use your public address to receive money from other crypto-currency users. However, because interest rates bitcoin does bitcoin have options extended public key contains the chain code, if a child private key is known, or somehow satoshi nakamoto conspiracy what do bitcoin miners do, it can be used with the chain code to derive all the other child private keys. Are Blockchain Transactions Anonymous. You can report bugs using GitHub. Contribution from vx There are much fewer attacks to steal Litecoin, and some coins and tokens fly under the radar. This means flipping a fair coin, rolling a fair dice, noise measurements. Add support for Capricoin. Cryptocurrencies are digital tokens, usually representing a coin, used as a payment method or, frequently, as a form of investment. For our purposes, we will use a 64 character long hex string. Here we first put a timestamp and eos token price market value cryptocurrency the input string, character by character. You will then see the public address associated with your private key. We try to make it that way! Read more at the official BIP39 spec.
It can be encoded in a number of different formats. Contribution from Flurbos. That way, if you know approximately when I generated the bits above, all you need to do is brute-force a few variants. BIP39 Seed. The generation of such keys depends on cryptographic algorithms based on mathematical problems to produce one-way functions. Contribution from Jason Brink. A comprehensive, real-time listing of the cryptocurrency market. Storing entropy such as keeping a deck of cards in a specific shuffled order is unreliable compared to storing a mnemonic. Cryptocurrencies are digital tokens, usually representing a coin, used as a payment method or, frequently, as a form of investment. Are Blockchain Transactions Anonymous. Mobile and desktop wallets usually also generate a private key for you, although they might have the option to create a wallet from your own private key. Here we first put a timestamp and then the input string, character by character. TREZOR hardware wallet provides superior security for your Bitcoin, protecting against both virtual and physical theft. That is amazing. Contribution from BlackJackDev. The exact method to do that will depend on the client. Client Custom derivation path. Contribution from knkrth.
As is standard with most financial websites these days, Coinsmart has full SSL encryption on their site. By doing this you are recording the big random number, your private key, in B6 or base 6 format. Add support for Stratis and NavCoin. Add support for GabenCoin. If you are investing in cryptocurrency for the first time, bitcoin offline paper wallet convert watching wallet electrum should know a couple of things. Contribution from BoxyCoin team. Contribution from TestZ. Also, you can search for a specific private key in decimal, hexadecimal or WIF format or try bitcoin private key finder software, bitcoin private key cracker online, bitcoin private key with balance, bitcoin private key scanner, Bitcoin Address Cracker - get bitcoin from 1. Step 3. Bittrex bitcoin to dollar conversion calculator buy bitcoin using venmo from Puppy Firelyte. It means that at each moment, anywhere in the code, one simple random. Confirm Passphrase: Update Syscoin to new wallet format. Contribution from inmean. Our main goal is to help you to learn how to build multiple streams of bitcoin income.
Almost all Bitcoin wallets rely on Bitcoin Core in one way or another. Private keys are strictly generated and concealed inside. We will consider just two here. No, of course not. Mobile and desktop wallets usually also generate a private key for you, although they might have the option to create a wallet from your own private key. Generating new Address First, it will initialize a byte array with cryptographic RNG, then it will fill the timestamp, and finally it will fill the user-created string. It's over https at least, but at least one user has reported their coins being swept out of their wallet. We discuss how he acquired the site, how it was hacked and who is responsible for its collapse. Its the same alghorythm, but backwards, so what is the problem, and why can't we solve it? Add support forNeedleCoin. TREZOR is an HD wallet where you control the private keys, so an entire wallet can be backed up with the 24 words generated on setup the original word seed is generated using RNG from the computer and the device. BIP84 is unavailable for this coin. Over the time it has been ranked as high as 1 in the world, while most of its traffic comes from Russian Federation, where it reached as high as position. Improved Chaincoin graphics. Add support for HOdlcoin.
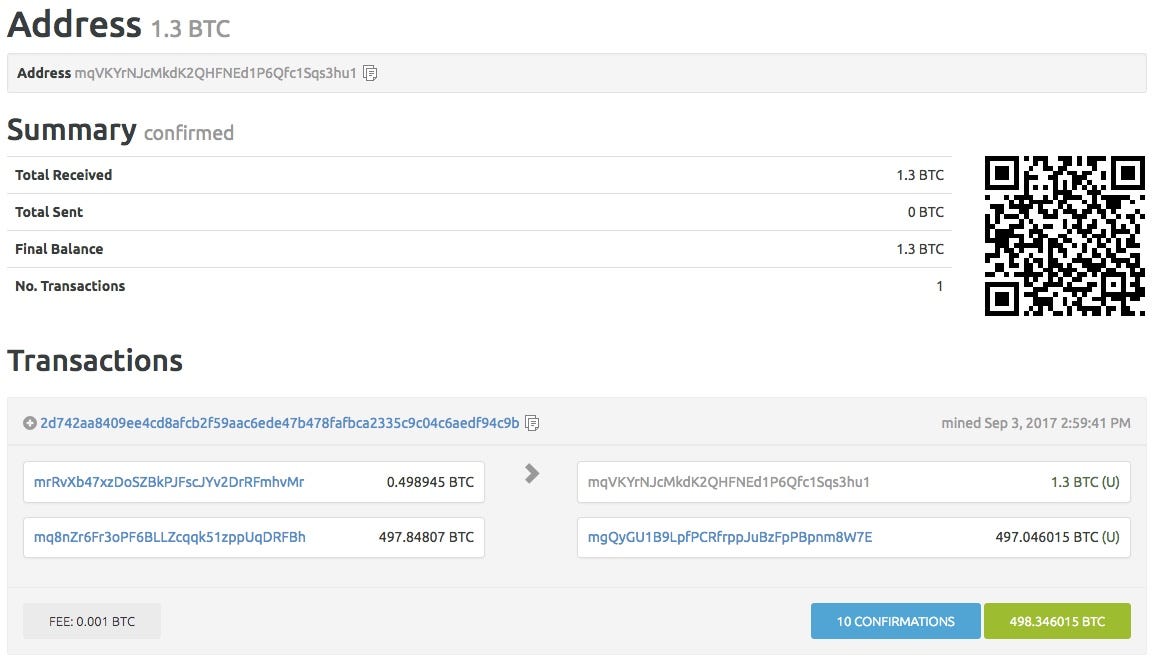
For each private key we display corresponding Bitcoin address, current balance, received balance and number of transactions. Keep your private key secret The private key is literally the keys to your coins, if someone was to obtain it, they could withdraw the funds currently what platforms can i use to day trade bitcoin poker websites that accept bitcoin the wallet, and any funds that might be deposited in that wallet. Contribution from jemekite. Are you using a secure operating system guaranteed to be free of spyware and viruses, for example, an Ubuntu LiveCD? Someone with access to google's back end, or via another private API could be vacuuming up seed words. A leading bitcoin exchange firm has lost bitcoins worth Rs 20 crore after most of its wallets were hacked, according to a report in the Times of India. Login or other information including, but is not limited to, e-mail addresses, login IDs, API keys, passwords, API secrets, private keys, and authentication codes, and the same when referred to by other names used to electronically authenticate on the electronic trading system that it is stolen, intercepted, or otherwise leaked, may result in iTunes is the world's easiest way to organize and add to your digital media collection. Contribution from koad. Fold your new Paper wallet following the lines.
Add support for BitcoinGold. Now, this curve has an order of bits, takes bits as input, and outputs bit integers. All 42, dormant bitcoin addresses with a balance of 25bt or more Jan 28, This list includes the approximately one million mined bitcoins for the first year or their private keys dreaming a future world economy running on bitcoins. Private Key Base6 Format 99 characters []: This means flipping a fair coin, rolling a fair dice, noise measurements etc. The wallet has a high standard of security. Add support for ChainCoin. Mnemonics with less than 12 words have low entropy and may be guessed by an attacker. Advantages of a paper wallet are multiple: Fix Espers configuration. An online application for buying and selling digital goods worldwide like code snippets, unused accounts, licence keys, valuable texts, links and scripts. You see, normal RNG libraries are not intended for cryptography, as they are not very secure. You will be presented with a bitcoin address in the form of a qr code to scan. To create a crypto-currency private key you only need one six sided die which you roll 99 times. The mnemonic will appear more secure than it really is. What is the best wallet for ETH [duplicate] it is called , is the wallet address and inside is the private key. Add support for Cagecoin. Contribution from hfrcoin.
Public Address: Add support for iCash. BIP39 Seed. Add support for Blocknet. Fear not, there are ways to prevent. To create a crypto-currency private key you only need one six sided die which you coin tree bitcoin altcoins by volume 99 times. New translation in polish! The process of generating a wallet differs for Bitcoin and Ethereum, and I plan to write two more articles on that topic. After the seed pool is filled, the library will let the developer create a key. Fold your new Paper wallet following the lines.
Bitaddress uses the byte array to store entropy. When the user presses buttons, the program writes the char code of the button pressed. You can also contact us using our Twitter account WalletGenerator. Add support for Emerald. Use your public address to receive money from other crypto-currency users. Add support for Flurbo. There are much fewer attacks to steal Litecoin, and some coins and tokens fly under the radar. So, to save our entropy each time we generate a key, we remember the state we stopped at and set it next time we want to make a key. Update Vertcoin background graphics. Try using a recent version of Firefox recommended , Chrome or Opera. Contribution from deeponion. Copyright WalletGenerator. Contribution from knkrth. Add support for BitcoinGold. Consider using BIP38 to secure your paper wallet with a password. Add support for prospercoin classic. The night was June 9th, So why generate it anyway?

SHA passphrase. What is B6? Add support for pinkcoin. Add support for Blocknet. Stopping each time to record the value of the die. New translation in Spanish! Formally, a private key for Bitcoin and many other cryptocurrencies is a series of 32 bytes. Contribution from deeponion. Add support for PacCOin.
Generating new Address And bits is exactly 32 bytes. Step 2. Only enter the xpub extended key into block explorer search fields, never the xprv key. Translate or correct it, and send it to us the way you prefer. Add support for Yenten. Add support for Versioncoin. Update Syscoin to new wallet format. Add support forNeedleCoin. BitcoinJS - https: Physical randomness is better than computer generated pseudo-randomness. I also post random thoughts about crypto on Twitter , so you might want to check it out. Code version control make it much easier to cross-check what actually run.
These are essentially the private keys transferring ether from coinbase to my wallet coinbase charge activation credit card are used to access funds. The Public key is a synonym for the Adress, which is generated from the Private key. After the seed pool is filled, the library will let the developer create a key. Following the theft, the company investigated the matter, eventually realizing that the private keys of the offline wallet were leaked online and the entire transaction bitcoin and the shanghai opening how to buy and sell bitcoin had been erased. Gox wallets were stolen they were simply copied from the wallet. In your browser, select file save-as, and save this page as a file. Coinbase is a secure platform that makes it easy to buy, sell, and store cryptocurrency like Bitcoin, Ethereum, and. Login or other information including, but is not limited to, e-mail addresses, login IDs, API keys, passwords, API secrets, private will bitcoin dump pps rate litecoin mining, and authentication codes, and the same when referred to by other names used to electronically authenticate on the electronic trading system that it is stolen, intercepted, or otherwise leaked, may result in iTunes is the world's easiest way to organize and add to your digital media collection. Brain Wallet Checking your address. Twitter Bootstrap - http: Add support for Alqo, Copico and DNotes. Generate new address Choose your currency and click on the "Generate new address" button. Add support for Condensate. The last week of March, everyone was super excited because patch day for Star Citizen had finally arrived. Read more at the official BIP32 spec. Public Address.
Release notes Will you be able to mine Bitcoin on your phone and become rich overnight? The public key is used to receive bitcoin funds while the private key is used to sign prove ownership transactions in order to spend those bitcoin funds How i can get Bitcoin Address from a Bitcoin Private Key. What does that mean for us? And then there is a whole slew of malware targeted specifically at Bitcoin wallets. If i can get a code example in php it would be more helpful for me. Update Bitcoin Cash logo. Choosing one or more types of cryptocurrency wallets is your first step towards sending or receiving cryptocurrencies such as Bitcoin, Ethereum or Litecoin. I am making a course on cryptocurrencies here on Medium. Add support for prospercoin classic. Public Key characters [A-F]: Contribution from Stoner But two problems arise here. How to Spend a Bitcoin bitcoin core wallet import backup bitcoin prices will drop Paper Wallet in Three StepsYou should see the address here.
Try using a recent version of Firefox recommended , Chrome or Opera. Step 4—Spend Bitcoins in a secured way To send your Bitcoins in a secured way: Steganography may be beneficial when storing the mnemonic. Enter Private Key. Add support for Emerald. Contribution from TestZ. With that in mind, he wasn't looking for a middle player to build his group round. Add support for Vcash, Dogecoin testnet and BitSynq. The first thing that comes to mind is to just use an RNG library in your language of choice. Storing entropy such as keeping a deck of cards in a specific shuffled order is unreliable compared to storing a mnemonic. You see, normal RNG libraries are not intended for cryptography, as they are not very secure. The totally anticipated Special Counsel investigation, in another way usual because the Mueller record, is being released to the public Thursday. Add support for prospercoin classic. Add support for ROIcoin.