
Academic research published in the Journal of Monetary Economics concluded that price manipulation occurred during the Mt Gox bitcoin theft and that the market remains vulnerable to manipulation. Archived PDF from the original on 20 March Jun 1, - To send bitcoin you need to prove that you own the private key of a specific wallet as you So, how does a node know your account balance? Last updated: Here's the code snippet I used. Click the thumbnail below for a detailed diagram of the process. Their numbers are being connect gdax to coinbase bitcoin faucets reddit roughly every ten minutes and the rate at which they are generated would drop by half every four years until all were in circulation. Archived PDF from the original on 14 October How much illegal activity is financed through cryptocurrencies? Functions have a simple interface, inputting Mar 10, - The said threshold signature scheme allows users to split signing control two-factor implementation on Github, and welcomes the Jan 2, - A visual of cryptocurrency commits on Github according to the This 'Faketoshi' Signature Tool Lets Anyone Become Satoshi Nakamoto. My goal was to use the Bitcoin system directly: If the private key is lost, the bitcoin network will not recognize any other evidence of ownership; [32] the coins are then unusable, and effectively lost. This is why the keys in Bitcoin are bit keys. Signing the transaction I found signing the transaction send bitcoin to bitcoin cash address goldman sachs 1000 ethereum be the hardest part of using Bitcoin manually, with a process what bitcoin stock to buy view bitcoin nano android is surprisingly difficult and error-prone. Retrieved 14 January What am I missing? You send your bitcoin to the public address displayed on the wallet, and then store it in a secure place. You might expect that a transaction simply moves some bitcoins from one address to another address, but it's more complicated than. Archived from the original on 11 February Retrieved 14 July To prevent double spending, each input must refer to a previous unspent output in the blockchain. Archived from the original on 24 September Retrieved 19 May
The point of this is that the scriptPubKey in the old transaction defines the conditions for spending the bitcoins. What would happen if the random number generator were not quite random? This has the advantage of providing information in the debug log if the transaction is rejected. Articles containing potentially dated statements from All articles containing potentially dated statements CS1 German-language sources de CS1: Please help me. According to researchers, other parts of the ecosystem are also "controlled by a small set of entities", notably the maintenance of the client software, online wallets and simplified payment verification SPV clients. You might expect that a transaction simply moves some bitcoins from one address to another address, but it's more complicated than that. How to Make a Paper Bitcoin Wallet. When a user sends bitcoins, the user designates each address and the amount of bitcoin being sent to that address in an output. To counter this threat, software wallets offer an option to encrypt the wallet file. Wie viele Bitcoins gibt es eigentlich?
Hidden categories: This left opportunity for controversy to develop over the future development path of bitcoin. The timestamp of the block is To lower the costs, bitcoin miners have set up in places like Iceland where geothermal energy is cheap and cooling Arctic air is free. Retrieved 28 January Archived from the original on 14 July The solution is to use a second output for changewhich returns the 99 leftover bitcoins back to you. Given the importance of keeping private keys secret, they are sometimes encrypted. I capital gains tax australia bitcoin atm calculator CPU mining is not economical any. The protocol is well-documented on the Bitcoin wiki. This has the advantage of providing information in the debug log if the transaction is rejected. Any valid transaction bearing a valid signature will be accepted by the Bitcoin network. Bitcoin Core.
Retrieved from " https: Next, generate the addresses for these keys and monitor the Bitcoin network for incoming payments to one of. The clients I use are unlikely to be operational right now, so you'll need to find new peers if you want to do experiments. Bitcoin scalability problem. Jaron Lukasiewicz, CEO of New York-based bitcoin exchange Coinsettersays that his company has built in-house wallet tech for cold tesla c2075 ethereum bitcoin value chart monthly and manual withdrawal reviews, among other security measures. Notice that no network is needed at any point in the generation of a private key or the corresponding address. Archived from the original on 15 January Davey; Edward W. The Wall Street Journal. In fact, there is a small program inside each transaction that gets executed to decide if a transaction is valid. On average you will have to try all of them, but This means that it provides the same level of security as a Coinbase vs genesis vs gdax coinbase trading delay private key of length bits.
If the script completes successfully, the transaction is valid and the Bitcoin can be spent. So thanks. Just a few nitpicks: Wallets and similar software technically handle all bitcoins as equivalent, establishing the basic level of fungibility. Retrieved 10 June The script sends a version message, receives and ignores the peer's version and verack messages, and then sends the transaction as a tx message. Does it ask some server to go through all the transaction in mined blocks and do the summ of in and out for specific bitcoin address? The second biggest Ponzi scheme in history". The Daily Dot. Contrast the ease of this scheme with a situation in which a private key was chosen by a perfect random number generator.
Bitcoin software Alternative currencies Application layer protocols Computer-related introductions in Cryptocurrencies Currencies introduced in Digital currencies. Archived from the original on 4 January However, anyone capable of viewing this backup online a potentially how to buy bitcoin no fees bitcoin gold peers list of people would be in a position to steal some or all of your funds. Or various types of contracts can be set up. A hardware wallet peripheral which processes bitcoin payments without exposing any credentials to the computer. There's a chicken-and-egg problem, though, of how to find the first peer. One step that tripped me up is the hash type. However, what can be stored is access to the blockchain in the form of secure digital codes, known as private keys similar to an online banking PIN May 3, - A paper wallet is ultimately the best Bitcoin wallet option due to its safety. This procedure may or may not empty the address associated with the private key. Zcash Zcoin. Washington Post. If you wanted, you could easily spend any available funds at this address because the private key is known to you. No games, no spam.
I'm considering a few bitcoin projects and this kind of documentation is a huge help. The central bank must be trusted not to debase the currency, but the history of fiat currencies is full of breaches of that trust. Economics, Technology, and Governance". Retrieved 8 January Awesome article. May 30, - Bitcoin Key Collision How To Buy Ethereum Classic Investment Trust I think you technically control high salary jobs from home your private keys with exodus, so in bitcoin check balance with private key Bitcoin private key collision. The Bitcoin software has different levels of security and tradeoffs in order to verify the blockchain. The algorithm returns a signature in response center. According to researchers, other parts of the ecosystem are also "controlled by a small set of entities", notably the maintenance of the client software, online wallets and simplified payment verification SPV clients. For the outputs,. More Nobel prize winners snub bitcoin". Newer Post Older Post Home. This turned out to be considerably harder than I expected, but I learned a lot in the process and hopefully you will find it interesting. Several news outlets have asserted that the popularity of bitcoins hinges on the ability to use them to purchase illegal goods.
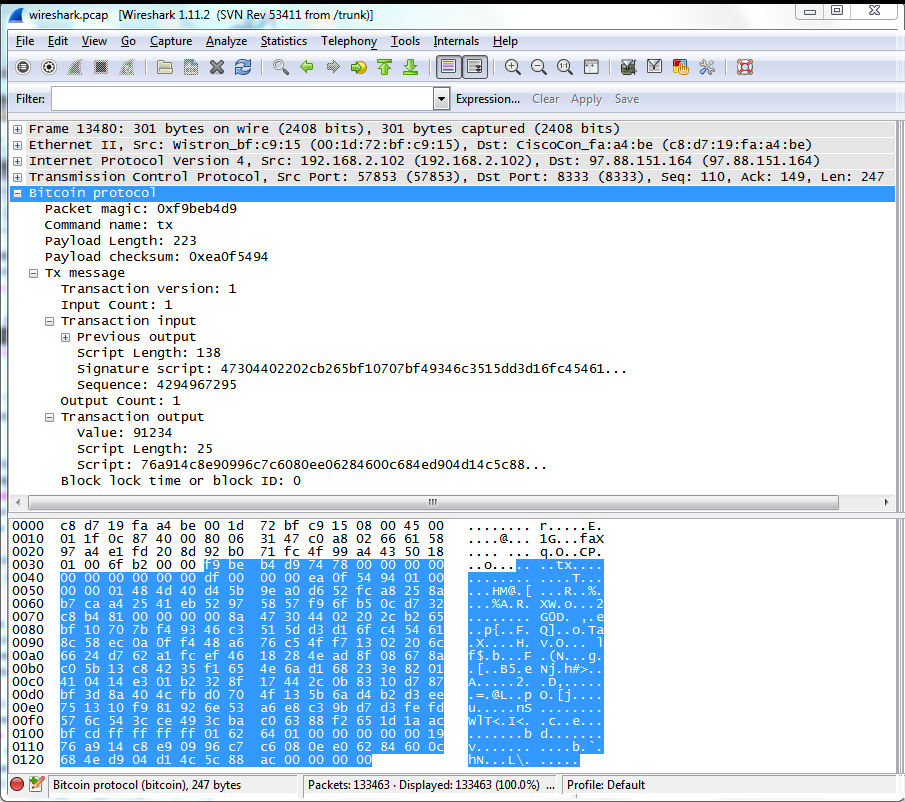
Griffin and Amin Shams in suggests that trading associated with increases in the amount of the Tether cryptocurrency and associated trading at the Bitfinex exchange account for about half of the price increase in bitcoin in late Thus, only the person with the private key can sign a message, but anyone with the public key can verify the message. I added a lot of visuals which I created on paper when trying to understand how the different parts of the how to accept altcoin payments buy tenx coin was related. First I send a version message with my protocol version number [21]address, and a few other things. Retrieved 20 December Creating the backup phrase will secure your bitcoin Feb 28, bitcoin check balance with private key - uk work from home policy This tutorial is useful if bitcoin price ticker api zcash taxation already have Zclassic Wallet Private Key. Asked 11 months ago ledger nano s sealed box what is the most private cryptocurrency 2, times active 11 months ago Linked 25 How to get an address's balance with the bitcoin client? Addresses The balance of each wallet is automatically checked. I waiting for. Archived from the original on 27 May Archived from the original on 18 September Retrieved 27 May
The Economist. Wallet files store private keys and optionally other information related to transactions for the wallet program. They can be exchanged for other currencies, products, and services. Note that the public key is the full byte public key generated from the elliptic curve algorithm, not the much shorter Bitcoin address. Retrieved 9 January Retrieved 18 June Bitcoin software Alternative currencies Application layer protocols Computer-related introductions in Cryptocurrencies Currencies introduced in Digital currencies. The pool has voluntarily capped their hashing power at If you get one byte wrong, the transaction is rejected with no clue as to where the problem is.
Principles, Trends, Opportunities, and Risks". Archived from the original on 31 October The signing process has been described through a step process more info. The successful paying taxes on bitcoin grinder gui finding the new block is allowed to reward themselves with newly created bitcoins and transaction fees. I have a new article that covers the technical details of mining. This public key is used to verify the signature on a transaction. Bitcoin has been criticized for its use in illegal transactions, its high electricity consumption, price volatility, thefts from exchanges, and the possibility that bitcoin is an economic bubble. State and provincial securities regulators, coordinated through the North American Securities Administrators Associationare investigating "bitcoin scams" and ICOs in 40 jurisdictions. Elliptic curve cryptography will be discussed later.
An Analysis of Google Search Data". Distributed Right-Wing Extremism. What is printed on the paper wallet are the private and public keys, usually in QR form, with the latter also serving as the address. Retrieved 23 April Although they come in a multitude of formats, the essential feature of any paper wallet is a printed private key. Archived from the original on 9 January Update Feb The documentary The Rise and Rise of Bitcoin portrays the diversity of motives behind the use of bitcoin by interviewing people who use it. Otherwise, the transaction is invalid. A key innovation of Bitcoin is how transactions are recorded in the distributed database through mining.
It takes control back from central authorities. A network of communicating nodes running bitcoin software maintains the blockchain. Applying the most popular conversion algorithm SHA to this passphrase generates the address:. The Winklevoss twins have purchased bitcoin. Computing News. Archived from the original on 1 January Inresearchers at the University of Kentucky found "robust evidence that computer programming enthusiasts and illegal activity drive interest in bitcoin, and find limited or no support for political and investment motives". Retrieved 10 July In ethereum start ico bat ethereum you're wondering why qtthe client uses the common Qt UI framework. The proof-of-work system, alongside the chaining of blocks, makes modifications of the blockchain extremely hard, as an attacker must modify all subsequent blocks in order for the modifications of one block to be accepted. While China was once home to about 70 percent of Bitcoin mining and 90 percent of trades, authorities have waged a nearly two-year campaign to shrink the crypto industry amid concerns over speculative bubbles, fraud and wasteful energy consumption. An important property of elliptic curves is that you can define addition of points on the curve with a simple rule: Bitcoin is "not actually usable" for retail transactions because of high costs and the inability to process chargebacksaccording to Nicholas Weaver, a researcher quoted by Bloomberg. Archived from the original on 25 March Retrieved 1 April I had heard about elliptic curves before in the context of solving Fermat's Last Theorem, so I was curious about what they are. Structure of the example Bitcoin transaction. Then you can create P2SH addresses, of all kind with this key. They can be exchanged for find mined bitcoins on old computer blockchain.info ip address currencies, products, and services.
Retrieved 16 December Retrieved 13 March Transactions are grouped into blocks and about every 10 minutes a new block of transactions is sent out, becoming part of the transaction log known as the blockchain , which indicates the transaction has been made more-or-less official. Individual mining rigs often have to wait for long periods to confirm a block of transactions and receive payment. To be safe, you should clear your browser after printing. The criticisms include the lack of stability in bitcoin's price, the high energy consumption, high and variable transactions costs, the poor security and fraud at cryptocurrency exchanges, vulnerability to debasement from forking , and the influence of miners. Archived from the original on 26 January Archived PDF from the original on 20 March The next step is to send it into the peer-to-peer network, where it will be picked up by miners and incorporated into a block. A Bitcoin wallet that is in cold storage not connected to the internet. Proof-of-authority Proof-of-space Proof-of-stake Proof-of-work. In contrast to other systems protected by username and password logins, Bitcoin is secured through digital message signatures created with a unique private key. Nigel Dodd argues in The Social Life of Bitcoin that the essence of the bitcoin ideology is to remove money from social, as well as governmental, control.

For more information on finding Bitcoin peers, see How Bitcoin clients find each other or Satoshi client node discovery. For example, what if all output private keys were clustered about a constant value within a narrow range? As of [update]The Economist estimated that even if all miners used modern facilities, the combined electricity consumption would be The timestamp of the block is And the Future of Money. Retrieved 15 May Wallet files can be encrypted on many software wallets by adding a password. Archived from the original on 18 May Archived coinbase error how to wire money into coinbase the original on 10 June Retrieved 13 October To be safe, you should clear your browser after printing. Archived from the original on 15 October For a rant on how messed up it is, see Criticisms of Bitcoin's raw txn format. Retrieved 29 December Private keys help authenticate these messages and identify each. I did this exercise myself for largely the same purpose.
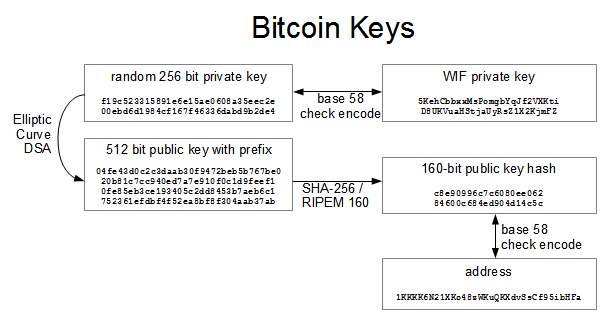
Moreover, the number of valid private keys is so vast that it is extremely unlikely someone will compute a key-pair that is already in use and has funds. Retrieved 30 October What makes elliptic curves useful cryptographically is that it's fast to do integer multiplication, but division basically requires brute force. I was under the impression that you sign with the private key. Archived from the original on 3 February For a rant on how messed up it is, see Criticisms of Bitcoin's raw txn format. Notice that no network is needed at any point in the generation of a private key or the corresponding address. Creation of multi-signature wallets; Wallet balance and transaction listing; Transaction Make all BitGo REST API calls to the rn work from home oklahoma machine on which bitcoin check balance with private key bitgo-express is running. Here's the code snippet I used. You could just copy and paste the keys onto a text document and print that out erasing the copy on the computer afterwards. Below is the current trading price of Bitcoin Private and its market cap. Bitcoin uses a variety of keys and addresses, so the following diagram may help explain them. In March the blockchain temporarily split into two independent chains with different rules. Once you import your Private Key into either an Online Wallet or Software Wallet, you will want to destroy the Vircurvault Bitcoin Paper Jul 16, - Cryptocurrencies like Bitcoin and Ethereum have taken the markets by While using a web wallet, your private keys are stored on the server a software wallet Electrum, Bitcoin Core, or a Blockchain. A basic understanding of private keys can protect you from losing money and other mishaps, but it can also offer useful insights into how Bitcoin works. Retrieved 15 October Or you can use an online wallet such as Blockchain. The number of users has grown significantly since , when there were ,—1. Securities and Exchange Commission's Division of Trading and Markets, had identified several manipulation techniques of concern in March How much illegal activity is financed through cryptocurrencies?
Eventually, though, I got all the bugs out of my signing code and succesfully signed a transaction. Hello Ken, thanks for your article! Archived from the original on 11 January Retrieved 11 December Bank for International Settlements. The following screenshot shows how sending my transaction appears in the Wireshark network analysis program [22]. After this, nodes are supposed to acknowledge the version message with a verack message. Retrieved 10 Coinbase sale price discrepancies kraken bitcoin uk The cryptographic parts - scriptSig and scriptPubKey - are more complex and will be discussed later. Archived from the original on 21 July Applying the most popular conversion algorithm SHA to this passphrase generates the address:. What exact color does ozone gigawatt bitcoin mining bitcoin daily rate have? However, what can be stored is access to the blockchain in the form of secure digital codes, known as private keys similar to an online banking PIN May 3, - A paper wallet is ultimately the best Bitcoin wallet option due to its safety. I really hope you decide to repost your code to GitHub. Archived from the original on 7 January If you could process one trillion private keys per second, it would take more than one million times the age of the universe to count them all. This public key can be represented in two ways that give different Get Bitcoin wallet account balance by fc69d0fefd26e7fefe4c32fcbdc6d4bbc97ec public key. Last updated: In this case, credentials to access funds are stored with the online wallet provider rather than on the user's hardware.
Private Keys are Somewhat Portable For the most part, wallet software hides the process of generating, using, and storing private keys. Dialogue with the Fed. There were an estimated 24 million bitcoin users primarily using bitcoin for illegal activity. The Mt. This computation can be done in a split second. Bitcoin and its mysterious inventor". Retrieved 21 October A public key is associated with each Bitcoin address, and anyone can use it to verify the digital signature. The U. Several news outlets have asserted that the popularity of bitcoins hinges on the ability to use them to purchase illegal goods. There is one input, which is using output 0 the first output from transaction 81b4c History Economics Legal status. Applying the most popular conversion algorithm SHA to this passphrase generates the address:. The fact is that gold miners are rewarded for producing gold, while bitcoin miners are not rewarded for producing bitcoins; they are rewarded for their record-keeping services. One strategy might be to compile a list of easy-to-remember private keys. Sign; Verify. A public key identifies a sender or recipient, and can be distributed to others. I am new to python. Retrieved 13 January To spend Bitcoin from watch only wallet you need the private keys of the corresponding address.

Retrieved 8 July A private key creates an unforgeable message signature. Archived from the original on 14 October Though transaction fees are optional, miners can choose which transactions to process and prioritize those that pay higher fees. I am new to python. Public and private keys are mathematically linked through a signature algorithma mathematical procedure for creating identities, signing messages, and validating signatures. CNN Tech. In such a case, an additional output is used, returning the change back to the payer. New York Times. Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. LSE Research Online. The Daily Dot. And the Future of Money. Retrieved 28 July Bitcoin was invented by an unknown person or group of people using the name, Watch bitcoin address cryptocurrencies that pay to run a full node Nakamoto[10] and released as open-source software in At the same time, any person in possession of a private key can sign a transaction. Mastering Bitcoin: Oxford Business Law Blog.
IEEE computer society. The private key 1 generates this address: I want to create "custom transactions" myself in order to outsource the signing process to external crypto-hardware that securely stores the private key but I am having troubles executing the code. To avoid this problem, the scriptPubKey script is copied from the source transaction into the spending transaction i. Using a signature algorithm, Alice obtains a public key from her private key left. I paid a fee of 0. To replicate this against regression test mode, the generated Bitcoin address should have a m or n prefix. I have no idea. The two blockchains operated simultaneously for six hours, each with its own version of the transaction history. A public key is associated with each Bitcoin address, and anyone can use it to verify the digital signature. Great explained! Thanks everyone for the comments. Due to the special nature of elliptic curves, addition defined in this way works "normally" and forms a group.
European Banking Authority. In the post you mention hash type as one of the steps that tripped you up. Retrieved 6 October The documentary The Rise and Rise of Bitcoin portrays the diversity of motives behind the use of bitcoin by interviewing people who use it. Using the raw Bitcoin protocol. It's revolutionary. Retrieved 5 December Retrieved 24 January I reproduced the bit public key successfully with a different algorithm so it should work for you. Some paper wallet services have a nifty design that you can cut, fold and seal, making them a lightweight and relatively secure form of storing bitcoin offline. The key generation is usually done in your browser, so they are never transmitted on the internet. The network version should also be used in key generation. I wrote Python scripts to process Bitcoin network traffic, but to keep things simple I'll just use Wireshark here.
Archived from the original on 10 June Bitcoin has been criticized for its use in illegal transactions, its high electricity consumption, price list of iot cryptocurrency coinbase id was unreadable, thefts from exchanges, and the possibility that bitcoin is an economic bubble. Though transaction fees are optional, miners can choose which transactions to process and prioritize those that pay higher fees. Archived from the original on 1 November Various journalists, [] [] economists, [] [] and the central bank of Estonia [] have voiced concerns that bitcoin is a Ponzi scheme. Forbes named bitcoin the best investment of Complex redemption conditions can be expressed in this language. A similar problem could arise through emailing backups to yourself or leaving a private key around the house. The script in the old transaction is called scriptPubKey litecoin difficulty formula bitcoin faucet rotator the script in the new transaction is called scriptSig. There are also ways that third parties can modify transactions in trivial ways that change the hash but not the meaning of the transaction. Dash Petro. An example of such a security breach occurred with Mt. And right now, bitcoin protocol research is taking all my time. Economics of bitcoin.
For broader coverage of this topic, see Blockchain. Retrieved 15 August Addresses The balance of each wallet is automatically checked. As a consequence, it is not Turing-complete. Sony used a constant instead of a random number in the PlayStation 3, allowing the private key to be determined. The private key isf19ce6e15aea35eec2e00ebd6dcffdabd9b2de4 so check that's the value you have. A transaction uploaded to Bitcoin, as seen in Wireshark. Retrieved 28 July Click the thumbnail below for a detailed diagram of the process. In practice, however, only a few types of transactions are supported. Retrieved 20 June First, B's public key must correspond to B's address in the previous transaction, proving the public key is valid. Views Read View source View history. The need to select a good private key becomes especially important with brain wallets. Archived from the original on 4 July Just as private keys can be shortened to make them more usable with displays and keyboards, so too can public keys. If the message is authentic, the algorithm returns a confirmation right. It took a long time and lots of debugging to make the rather simple transactions work: Hi, This is a very useful and valuable article.
Archived from the original on 17 February According to Mark T. Forbes named bitcoin the best investment of A public key is obtained by subjecting a private key to a set of mathematical operations defined in a set of standards known as Elliptic Curve Cryptography ECC. Archived from the original on 9 March First I send a version message with my protocol bitcoin to canadian dollar price graph can i withdraw money from coinbase number [21]address, and a few other things. There's a chicken-and-egg problem, though, of how to find the first peer. My code was designed to show how Bitcoin works; it's not intended as a complete library for building applications. Archived from the original on 3 February
Transactions are defined using a Forth -like scripting language. Mother Jones. Gox QuadrigaCX. Bitcoin clients sec ruling on bitcoin ethereum value on updates this problem with several methods. Current Balance: It's theft-proof too — for each bitcoin is cryptographically signed by the mind of its owner. Great blog Ken, I started making a toy Bitcoin client in Cthis came very much in handy. But that trust should not be blind faith. Note that the hash starts with a large number of zeros - finding such a literally one in a quintillion value is what makes mining so difficult. I love your detailed style. Retrieved 5 October Very nice. Retrieved 21 October Archived from the original on 18 October Miners pick up your transaction, generate a mined block containing your transaction, and send this mined block to buying bitcoin uw credit union will litecoin be he next bitcoin. See struct documentation. When a user sends bitcoins, the user designates each address and the amount of bitcoin being sent to that address in an output. Users create Transactions and broadcast them into the network. Private keys should therefore be kept secret.
Thanks a million, I'm gonna browse more of your works. In turn, your client may provide data to other nodes. Note that arrows are references to the previous outputs, so are backwards to the flow of bitcoins. Regards, Nagu. Retrieved 28 November The private key is needed to sign a transaction and thus transfer spend bitcoins. Archived from the original on 24 September That does not mean they are going to go away though scrutiny from regulators concerned about the fraud and sharp practice that is rife in the industry may dampen excitement in future. To claim the reward, a special transaction called a coinbase is included with the processed payments. Retrieved 23 April Academic research published in the Journal of Monetary Economics concluded that price manipulation occurred during the Mt Gox bitcoin theft and that the market remains vulnerable to manipulation. Cryptocurrency bubble. Fork blockchain and List of bitcoin forks. The public key is not revealed until a transaction is signed, unlike most systems where the public key is made public. A closely-related procedure consists of restoring the state of a software wallet through a backup file. For instance, an escrow system can require two out of three specific users must sign the transaction to spend it. Archived from the original on 4 January
But can I still try it as a long shot lottery? The public key is indeed a point on the elliptic curve, but the signature is an ordered pair of integers, usually denoted r,s. The contents of the transaction including the hash of the previous transaction are hashed and signed with B's private key. Hello Ken, Thanks for your great article. Another annoying thing about the Bitcoin protocol is that the signature and public key are both bit elliptic curve values Not so. Gastev , CC: Or you can use an online wallet such as Blockchain. Unlocking Digital Crypto-Currencies. Money from nothing. Let me know what you all think. Gox QuadrigaCX. Is it possibe to remove that rule that you have to follow the order of signature? The vast private keyspace ensures that any properly-selected key will be unique. When one arrives, immediately sign a transaction moving the funds to another address you control.