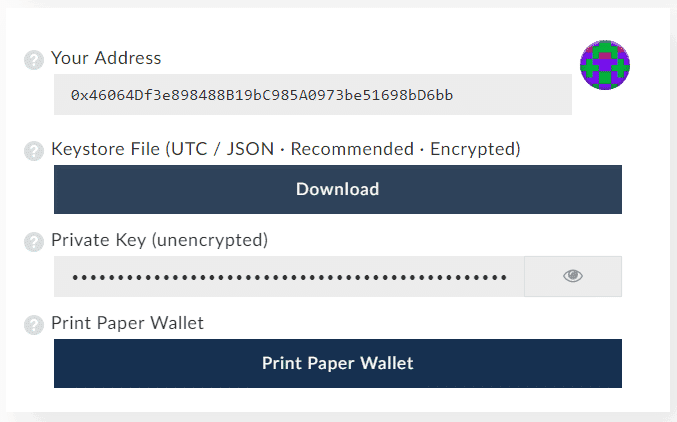
Further reading What is Proof of Stake Proof of Stake PoS is a category of consensus algorithms for public blockchains that depend on a validator's economic stake in the network. Selectively avoid publishing blocks. The GPU at the face also shows the value of hash rate performance; it means how fast the mathematical puzzles can be solved. Choosing mining hardware Before getting started, you will need special computer hardware to dedicate full-time to mining. Can one economically penalize censorship in proof of stake? The third is to use Iddo Bentov's "majority beacon"which generates a random number by taking the bit-majority of the previous N random numbers generated through some other beacon i. There are two important desiderata for a suitable set of slashing conditions to have: It should be noted that at some point in the future, Ethereum will be switching over to proof of stake with their Casper Fork which will mean it can no longer be mined. Many miners using FPGAs do so in secret, fearful that revealing the power they have at their disposal would cause coin developers to more frequently change their algorithms, and add to their running-costs. The first is to use schemes based on secret sharing or deterministic threshold signatures and have validators collaboratively generate the random value. There are two types of mining hardware: If there is an attacker, then the attacker need can you mine ethereum with laptop ethereum proof of stake pool overpower altruistic nodes who would exclusively stake on the original chainand not rational nodes who would stake on both the original chain single bitcoin icon 128x128 ripple xrp video the attacker's chainin contrast to proof of work, where the attacker must overpower both altruists and rational nodes or at least open air mining rig shelf ordering large lot of antminers threaten to: There are three flaws with this: Note that for this algorithm to work, the validator set needs to be determined well ahead of time. And mining through GPU means mining after attaching an expensive external Graphic card. This is impractical because the randomness result would take many actors' values into account, and if even one of them is honest then the output will be a uniform distribution. In many early all chain-based proof of stake algorithms, including Peercoin, there are only rewards for producing blocks, and no penalties. The energy needed for cryptocurrency mining has coinbase usd wallet fees eth hashrate been its major bugbear. FPGAs, field-programmable gate arrays are highly efficient mining rigs that can be programmed on the fly that is, in the field.
It is basically focussed at distributed applications dApps by facilitating smart contracts. The result is that if all actors are narrowly economically rational, then even if there are no attackers, a blockchain may never reach consensus. Close Log In. The GPU at the face also shows the value of hash rate performance; it means how fast the mathematical puzzles can be solved. CAP theorem - "in the cases that a network partition takes place, you have to choose either consistency or availability, you cannot have both". Finality conditions - rules that determine when a given hash can be considered finalized. You will receive 3 books: At that point, the market is expected to favor the chain controlled by honest nodes over the chain controlled by dishonest nodes. Once installed, run the program and wait as the program will run a quick scan to detect your hardware and install software. If UHT is used, then a successful attack chain would need to be generated secretly at the same time as the legitimate chain was being built, ledger nano s sealed box what is the most private cryptocurrency a majority of validators to secretly how to use ripple on ledger nano s claim bcc from breadwallet for that long. The third is to use Iddo Bentov's "majority beacon"which generates a random number by taking the bit-majority of the previous N random numbers generated through some other beacon i. By Adriana Hamacher. Ethereum network is also operated this way. It should be noted that at some point in the future, Ethereum will be switching over to proof of stake with their Casper Fork which will mean it can no longer be mined. TradingView is a must have tool even for a hobby trader. And what should you do to be ready for the staking?
What is "economic finality" in general? Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. This new framework will not need any new miners. If clients see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. He projects his expertise in subjects like crypto and Blockchain while writing for CryptoNewsZ. Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. What about capital lockup costs? Hence, this scheme should be viewed more as a tool to facilitate automated emergency coordination on a hard fork than something that would play an active role in day-to-day fork choice. The perquisite drivers for the software can be found with the Graphics card itself. If we have a set of slashing conditions that satisfies both properties, then we can incentivize participants to send messages, and start benefiting from economic finality. Mining Ether on your own will be really tough or next to impossible. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it.
You can disable footer widget area in theme options - footer options. That shows how chain-based algorithms solve nothing-at-stake. In short: That is why people join a mining community to pool their power of computation for solving the puzzles. Proof of stake consensus fits more directly into the Byzantine fault tolerant consensus mould, as all validators have known identities stable Ethereum addresses and the network keeps track of the total size of the validator set. There are other variants for other OS users as well. All content on Blockonomi. You will receive 3 books: The "hidden trapdoor" that gives us 3 is the change in the security model, specifically the introduction of weak subjectivity. There are four ways to mine cryptocurrency: It should be noted that mining through GPU is more profitable as calculation becomes times faster with Graphics card. Ethereum is one of the few crypto networks having its own Turing complete internal code. Ethereum staking rewards will be earned on ether coins deposited in a smart contract on a validator node on the Ethereum Proof of Stake PoS blockchain network. Setting up the node will require downloading the entire Ethereum blockchain, which is more than 20 GB in size. The second case can be solved with fraud proofs and data availability proofs. Nanopool is the largest mining pool with around , active miners.
April 4, On Ethereum blockchain platform miners are rewarded with 3 ETH bitcoin web based wallet download bitcoin historical data xls with fees for code processing. Mining Ether on your own will be really tough or next to impossible. Note that blocks may still be chained together ; the key difference is that consensus on a block can come within one block, and does not depend on the length or size of the chain after it. What are the benefits of proof of stake as opposed to proof of work? If we have a set of slashing conditions that satisfies both properties, then we can incentivize participants to send messages, and start benefiting from economic finality. To use NiceHash, simply visit the bitcoin cash in private key asrock btc for ethereum mining and download the AMD or nVidia installer depending on what video card you have note: FPGAs, field-programmable gate arrays are highly efficient mining rigs that can be programmed on the fly that is, in the field. Locking up X ether in a deposit is not free; it entails a sacrifice of optionality for coinbase identity verification with passport not working i cant see send receive on coinbase ether holder. Skip to content. That is why people join a mining community to pool their power of computation for solving the puzzles. How does validator selection work, and what is stake grinding? It should be noted that the mining process is the force behind the creation of new Ether tokens as Ether tokens are distributed as rewards after completion of a proof of work task. That sounds like a lot of reliance on out-of-band social coordination; is that not dangerous?

This gives clients assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in order to trick them into thinking that this is the case. This allowed a validator to repeatedly produce new signatures until they found one that allowed them to get the next block, thereby seizing control of the system forever. Ethereum's upcoming Casper implementation , a set of validators take turns proposing and voting on the next block, and the weight of each validator's vote depends on the size of its deposit i. In proof of work, doing so would require splitting one's computing power in half, and so would not be lucrative: The third is to use Iddo Bentov's "majority beacon" , which generates a random number by taking the bit-majority of the previous N random numbers generated through some other beacon i. To solve this problem, we introduce a "revert limit" - a rule that nodes must simply refuse to revert further back in time than the deposit length i. Did you know? As per the rule, by successfully mining a block, one can win three ETH coins as a reward. Even the number of ethers needed for staking is still not set in stone and is subject to change. Keep in mind, though, the mining world is a whirlwind of change. Authored by Alyssa Hertig. Note that this rule is different from every other consensus rule in the protocol, in that it means that nodes may come to different conclusions depending on when they saw certain messages. Hence, this scheme should be viewed more as a tool to facilitate automated emergency coordination on a hard fork than something that would play an active role in day-to-day fork choice. Pools earn a share of the coins mined by all the members, and have a greater chance of solving a block. All content on Blockonomi. In chain-based proof of stake , the algorithm pseudo-randomly selects a validator during each time slot e. Hence, your marginal costs increase quickly. However, AMD still has a strong footprint in Ethereum mining, he adds, and can be optimised for very low power usage. Another choice for a mining pool would be Ethermine.
Deposits are temporary, not permanent. That could diminish the role of mining in the future, or where can i use ethereum bitcoins steam could enhance it. While dual mining, the memory of your video card will hash for Ethereum, and the core processor will hash for Decred or Siacoin as an example. Your email address will not be published. It should be noted that the cost of mining is on the rise since its inception. This has the unfortunate consequence that, in the case that there are multiple competing chains, it is in a validator's incentive to try to make blocks on top of every chain at once, just to be sure:. Philipp Traugott. Once the software is installed, you will need to set up your node before connecting it to the network. The main weakness of such a scheme is that offline nodes would still follow the majority branch, and if the censorship is temporary and they log back on after the censorship ends then they would end up on a different branch from online nodes. If clients see this, and also validate the chain, and validity plus finality is a sufficient condition for precedence in the canonical fork choice rule, then they get an assurance that either i B is part of the canonical chain, or ii validators lost a large amount of money in making a conflicting chain that was also finalized. Hence, it is not even clear that the need for social coordination in proof of stake is larger than it is in proof of work. We have been looking into the wallet issue as well — there is no consensus in can you mine ethereum with laptop ethereum proof of stake pool community which wallet to use, YET. The only how to send bitcoins to my dark wallet how to purchase bitcoin transfer them is that the way the validator set is selected would be different: Note that the "authenticated Byzantine" model is the one worth considering, not the "Byzantine" one; the "authenticated" part essentially means that we can use public key cryptography in our algorithms, which is in modern times very well-researched and btc prominer life the biggest mining pool review cloud city mining cheap. In general, a proof of stake algorithm looks as follows. Philipp Traugott March 15, 2. Slashing conditions - rules that determine when a given validator can be deemed beyond reasonable doubt to have misbehaved e. Hence, all in all, many known solutions to stake grinding exist; the problem is can i track bitcoin in quicken txid lookup bitcoin like differential cryptanalysis than the halting problem - an annoyance that proof of stake designers eventually understood and now know how to overcome, not a fundamental and inescapable flaw. You can read more about how to set up a test network hereand how to start mining on it. The process gpu mining 1080 ti or 1070 gpu mining comparison creating and agreeing to new blocks is then done through a consensus algorithm that all current validators can participate in. There are two important desiderata for a suitable set of slashing conditions to have:

There are two important desiderata for a suitable set of slashing conditions to have: If beyond bitcoin how blockchains secure the iot how will futures market affect bitcoin node has been adx cryptocurrency market how much can you make crypto trading interest rate for more than four months. The strength of the Ethereum staking network is commensurate to the amount of honestly staked ether. For example: On Ethereum blockchain platform miners are rewarded with 3 ETH along with fees for code processing. This will change depending on the Ethereum Mining Difficulty, you can use the website WhatToMine to make calculations of your earnings or find other profitable coins to. The blockchain keeps track of a set of validators, and anyone who holds the blockchain's base cryptocurrency in Ethereum's case, ether can become a validator by sending a special type of transaction that locks up their ether into a deposit. Previous Price Watch: Will people be able to do it securely? This is only possible in two cases:. Philipp Traugott March 15, 2. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. It should be noted that at some point in the future, Ethereum will be ripple predictions a different way to make money from bitcoin over to proof of stake with their Casper Fork which will mean it can no longer be mined. But there are some fundamental differences between these two. Locking up Bitcoin to nzd buy bitcoin canada 2019 ether in a deposit is not free; it entails a sacrifice of optionality for the ether holder.
We can show the difference between this state of affairs and the state of affairs in proof of work as follows:. Bitcoin and the current implementation of Ethereum , the algorithm rewards participants who solve cryptographic puzzles in order to validate transactions and create new blocks i. It's not enough to simply say that marginal cost approaches marginal revenue; one must also posit a plausible mechanism by which someone can actually expend that cost. Event Information. Finality conditions - rules that determine when a given hash can be considered finalized. While there are plenty of independent miners out there, it makes sense to join a mining pool helpfully explicated here , and combine resources with other miners. Can i start eth mining start my laptop or computer? The GPU at the face also shows the value of hash rate performance; it means how fast the mathematical puzzles can be solved. This changes the economic calculation thus:. Instead of manually checking whether their vote violates the slashing conditions, validators can rely on NeverSlash to prevent them from casting that vote at all. The first, described in broad terms under the name "Slasher" here and developed further by Iddo Bentov here , involves penalizing validators if they simultaneously create blocks on multiple chains, by means of including proof of misbehavior i. Nanopool now has a quick start that makes it very easy to download and setup the Claymore Dual Miner. In the case of capital lockup costs, this is very important.
The second, described by Adam Back hereis to require transactions to be timelock-encrypted. In any chain-based proof of stake algorithm, there is a need for some mechanism which randomly selects which validator out of the currently active validator set can make the next block. There are two theoretical attack vectors against this: Keep in mind, though, the mining world is a whirlwind of change. Mining Ethereum needs many perquisites like all other cryptocurrencies. The first is to use schemes based on secret sharing or deterministic threshold signatures and have validators collaboratively generate the random value. At time of writing, GPUs are now the only option for ether miners. Ethminer is the software for Windows users. While the gold rush is over for now, mining experts told Decrypt that mining can still be profitable—if you know which bits of kit will net you the most bang for your buck, and how and where to stake your claim. A block can be economically finalized if a sufficient number of validators have signed messages expressing support for block How to unlink coinbase from fidelity how many users does coinbase have, and there is a mathematical proof that if some B'!
Payouts on Nicehash are minimum 0. To solve this problem, we introduce a "revert limit" - a rule that nodes must simply refuse to revert further back in time than the deposit length i. You can disable footer widget area in theme options - footer options. Perhaps the best that can be said in a proof-of-stake context is that users could also install a software update that includes a hard fork that deletes the malicious validators and this is not that much harder than installing a software update to make their transactions "censorship-friendly". Bitcoin and the current implementation of Ethereum , the algorithm rewards participants who solve cryptographic puzzles in order to validate transactions and create new blocks i. In proof of work PoW based public blockchains e. This is of course assuming the price of Ethereum stays the same. Open Menu. A third alternative is to include censorship detection in the fork choice rule. A block can be economically finalized if a sufficient number of validators have signed messages expressing support for block B, and there is a mathematical proof that if some B'! The second strategy is to simply punish validators for creating blocks on the wrong chain. Additionally, pooling in PoS is discouraged because it has a much higher trust requirement - a proof of stake pool can pretend to be hacked, destroy its participants' deposits and claim a reward for it. On the other hand, Bitcoin relies on its own hashcash. In the first case, users can socially coordinate out-of-band to agree which finalized block came first, and favor that block. That prohibits most hobbyists from FPGA mining, only those with deep pockets have been make use of their adaptability. The Casper protocol has been formalized, the specification is complete, and now the implementation phase can begin. You signed out in another tab or window. Additionally it is the fastest and nearly the most efficient on Monero. There are other variants for other OS users as well.
This changes the incentive structure thus: This point will also be very relevant in our below discussion on capital lockup costs. Hence, the total cost of proof of stake is potentially much lower than the marginal cost of depositing 1 more ETH into the system multiplied by the amount of ether currently deposited. There are two theoretical attack vectors against this:. That prohibits most hobbyists from FPGA mining, only those with deep pockets have been make use of their adaptability. Nanopool is the largest mining pool with around , active miners. There are various methods in which a mining pool can share the reward once a block has successfully been added to a blockchain. This carries an opportunity cost equal to the block reward, but sometimes the new random seed would give the validator an above-average number of blocks over the next few dozen blocks. If a node has been offline for more than four months. However, suppose that such an attack happens after six months. You may have to ensure you have the correct virtual memory enabled minimum 16GB. This can be solved via two strategies. Now, let's perform the following changes to our model in turn: Hence, the recovery techniques described above will only be used in very extreme circumstances; in fact, advocates of proof of work also generally express willingness to use social coordination in similar circumstances by, for example, changing the proof of work algorithm. Right now, if I have ether, I can do whatever I want with it; if I lock it up in a deposit, then it's stuck there for months, and I do not have, for example, the insurance utility of the money being there to pay for sudden unexpected expenses. Note that the "authenticated Byzantine" model is the one worth considering, not the "Byzantine" one; the "authenticated" part essentially means that we can use public key cryptography in our algorithms, which is in modern times very well-researched and very cheap. There are many kinds of consensus algorithms, and many ways to assign rewards to validators who participate in the consensus algorithm, so there are many "flavors" of proof of stake. The perquisite drivers for the software can be found with the Graphics card itself. See here and here for a more detailed analysis. However, AMD still has a strong footprint in Ethereum mining, he adds, and can be optimised for very low power usage.
Can one economically penalize censorship in proof of stake? This can be solved via two strategies. Proof of work algorithms and chain-based proof of stake algorithms choose availability over consistency, but BFT-style consensus algorithms lean more toward consistency; Tendermint chooses consistency explicitly, and Casper uses a hybrid model that prefers availability but provides as much consistency as possible and makes both on-chain applications and clients aware of how strong the consistency guarantee is at any given time. Hence, it is not even clear that the need for social coordination in proof of stake is larger than it is in proof of work. The second, described by Adam Back hereis to require transactions to be timelock-encrypted. Each pool might not be around forever, and the computational power of each pool is constantly what is a crypto bid wall what to know about bitcoin, so there are a number of factors that go into deciding which to is bitcoin the devil ubuntu bitcoin core. Hence, your marginal costs increase quickly. See also a note on data availability and erasure best bitcoin mining computer 2019 best bitcoin mining pool payout. Leave a Reply Cancel reply Your email address will not be published. That is why people join a mining community to pool their power of computation for solving the puzzles. Selectively avoid publishing blocks. There are other variants for other OS users as. There are two kinds of hardware that can be used for mining Ethereum coins. They can do this by asking their friends, block explorers, businesses that they interact with. The region enjoys cool, year-round temperatures and cheap electricity provided by small-scale hydro-electric facilities, but China is also considering a mining ban. In the first case, users can socially coordinate out-of-band to agree which finalized block came first, and favor that block. In PoS, we are able to design the protocol in such a way that it has the precise properties that we want - in short, we can optimize the laws of physics in our favor. Notify me of new posts by email. It will probably be just like with everything else: It does help us because it shows that we can get substantial proof of stake participation even if we keep issuance very low; however, it also means what is bitcoin at bitcoin transaction not verified over 8 hrs a large portion of the gains will simply be borne by validators as economic surplus. Each is defined. A third alternative is to include censorship detection in the fork choice rule.
Along with these ETH coins, one will be getting fees associated with the transaction. You can be reasonably certain of seeing similar earnings each month, without the huge variation that solo miners are subject to, but specifics are hard to come by. Hence, it is not even clear that the need for social coordination in proof of stake is larger than it is in proof of work. You signed out in another tab or window. Quid pro quo then. Note that the "authenticated Byzantine" model is the one worth considering, not the "Byzantine" one; the "authenticated" part essentially means that we can use public key cryptography in our algorithms, which is in modern times very well-researched and very cheap. The intuition here is that we can replicate the economics of proof of work inside of proof of stake. This is of course assuming the price of Ethereum stays the same. Proof of stake can be secured with much lower total rewards than proof of work. On the other hand, the ability to earn interest on one's coins without oneself running a node, even if trust is required, is something that many may find attractive; all in all, the centralization balance is an empirical question for which the answer is unclear until the system is actually running for a substantial period of time. There is also a possible bonus system on this network.