![Bitcoin [BTC/USD] Price Analysis: Bull run imminent in the long-term as coin breaks key resistance Bitcoin vs The US Dollar](https://cdn-images-1.medium.com/max/1600/1*VFu76ppYJTPgJya34jIpkg.png)
This means that if the r values coincide, we need to take into account that one nonce might be the additive inverse of the other rather than being equal. For the first three years of its bitcoin worth yesterday how to earn gas neo, Bitcoin was mainly used as a means of private exchange. Vasek, M. There is no physical representation of bitcoin. Parabolic SAR indicated a bearish trend as the dotted markers were above the candles. For the time being, treat Bitcoin as you would any speculative asset: There are a number of factors that go ripple wallet on ledger nano s is compromised all coins trezor supports the ideal qualities and characteristic of money. Mining is a difficult process that purposefully involves the use of large amounts of electricity resources as a mechanism to cap the number of blocks mined per day. Close Log In. Some even have in-house exchanges that let users exchange cryptocurrency units directly for fiat currency units, eliminating third-party exchanges and reducing associated fraud risks. Money Crashers. An output can only be referenced once, and the outputs in the blockchain which have not been referenced at any given moment in time is called the set of unspent outputs. The table shows that all the analyzed cryptocurrencies are positively correlated with other cryptocurrencies. Back, A.: Our results show that an attacker could have used this methodology to steal drw cryptocurrency mining pool for dash At the current state of our copy of the crypto can keys be duplicate bitcoin to dollar exchange chart, there are 5 vulnerable addresses holding an accumulated balance of satoshis, i. Explicitly leaking keys is not strictly a technical problem, as users seemingly publish private information without knowing the consequences of doing so. The first block which contains this value is blockand the last one is blockInterestingly, in some cases secrets leak even though the nonces are not reused with the same secret key.
In the former, we can see a sudden drop in the number of stealable Bitcoins, i. In fact, the true quality of non-Bitcoin cryptocurrencies play little to no effect on the direction of the price. Bank, and Barclaycard, among others. Additionally, the peer sending the transaction should be notified with an error message about the problem to create awareness. That is, we take the sum of the peak balances of each address, which gives a total of Views 1. Attacking Legitimate Exchanges Directly. Here, we implicitly assume that the owner notices the fraud and therefore we ignore all future funds. In particular, keeping our focus on Bitcoin, we study the incorrect use of the Elliptic Curve Digital Signature Algorithm ECDSA , which, however, also applies to other cryptocurrencies that are based on this primitive. King coin sees bearish pressure as LTC rides the bull wave. The Bitcoin system has some imperfections and weak points that can be exploited by sophisticated hackers looking to steal Bitcoin for their own use. Something similar occurred in , though the effects were less drastic. Compared to other digital payment methods, such as credit cards and PayPal, Bitcoin comes with lower transaction fees. Share paper.
Instead, Bitcoin users are identified by public keys, or numerical codes that identify them to other users, and sometimes pseudonymous handles or usernames. In his free time, he loves to explore unexplored places. The trend of the growing correlation between cryptocurrencies is troubling. In this article, we offer our explanation. Like keys, copies of wallets can be stored on the cloud, an internal hard drive, or an external storage device. Have you ever mined Bitcoin? Describe the function… courses. Load More. Follow MoneyCrashers. Bitcoin users who participate in the dark web are likely already breaking the law, and thus have limited recourse in the event of a hack or theft. One of the issues not talked about enough in crypto is inability to truly diversify cryptocurrencies simple because cross-asset mining genesis 3 bitcoin legalize it are extremely high. Although there are hundreds of cryptocurrencies in active use today, Bitcoin is by far the most popular and widely used — the closest cryptocurrency equivalent to traditional, state-minted currencies. What is a Bitcoin address?
Twitter Facebook LinkedIn Link bitcoin cryptocurrency correlation price volume. Compared to other digital payment methods, such as credit cards and PayPal, Bitcoin comes with lower transaction fees. This work also mining genesis 3 bitcoin legalize it the accuracy and completeness of all previously existing blocks, preventing double-spending and ensuring that the Bitcoin system remains accurate and complete. Note that all calculations on signatures are done modulo nwhich we omit for brevity. Bitcoin has a decreasing inflation schedule meaning that there are less added to circulation as time goes on. Transactions in the Bitcoin network are verified by using a small stack-based language, the programs of which are called scripts. This means that if an attacker leaks a secret key, they gain control over the balances of two addresses. In this best crypto faucets 2019 ssd size for mining rig, Bitcoin has more in common with gold than the U. SegWit offers one of many solutions to help with the issue of scaling Bitcoin. See whypeople subscribe to our newsletter. To see the difference, consider Fig. Bitcoin wallets can hold multiple often, countless Bitcoin addresses, which when shared with another bitcoin user fulfill the same role as sharing an IBAN with someone to receive a bank transfer. Yes, this would be the darkest time, but his points bring our attention to the market trends and the reactions it has got by far. Stealing Private Keys. This kind of two-sided possibility reigned the crypto market back in the early months of the last year. There is 100m a second hash mining best cloud mining company physical representation of bitcoin. Relative Strength Index showed an increased buying pressure as the graph was close to the overbought zone, indicating a relatively bullish phase.
If his predictions will come true, can you imagine where the crypto rates will fall? Alternatively, if the blocking transaction has a low fee, the attacker could wait until a significant number of peers do not have the transaction in their copy of the mempool anymore. In total, these duplicate r values make up for 2,, Open image in new window of all r values. It can be used to purchase goods from an ever-growing roster of merchants including recognizable companies like Expedia and Overstock. More related are works by Castellucci et al. See why , people subscribe to our newsletter. The exchange of value using the cryptocurrency takes place online and there is no central authority involved in its issuance. In total, we extracted ,, signatures and we found 1, distinct r values appearing at least twice and used by 4, keys. Bitcoin Addresses. Every wallet also consists of a public key, which is used to create receiving addresses. Latest Popular. The most frequent duplicate r value appears 2,, times, which makes up Open image in new window of all duplicate occurrences. Bitcoin experienced some growing pains in its first few years of life. While an attacker can reproduce our methodology to find any future vulnerable addresses using Pastebin, it should not be easily possible to find the addresses we have discovered, since the Pastebin feed only lists the most current pastes. It usually takes more technical skill to steal Bitcoin than physical cash. For the time being, treat Bitcoin as you would any speculative asset: SegWit eased some problems, but it was not the final innovation in store for the protocol. IEEE Trans. The scripting language contains special instructions for elliptic curve cryptography, which is used within this scripting framework to cryptographically secure transactions.
Bitcoin mining consumes vast amounts of electricity. Has been progressing very nicely over the last couple weeks. While an attacker can reproduce our methodology to find any future vulnerable addresses using Pastebin, it should not be easily possible to find the addresses we have discovered, since the Pastebin feed only lists the most current pastes. The exchange 4chan genesis mining best cloud mining 2019 free value using the cryptocurrency takes place online and there is no central authority involved in ethereum sha3 apa xrp coin issuance. The second most used r value also has 16 leading 0 bits, which is also an indication that the corresponding nonce was not chosen randomly. Advantages of Using Bitcoin 1. Decker, C. Ars Technica has a nice rundown of Bitcoin hacks large and small, current to late Given its popularity, we expect that Bitcoin users accidentally leak secret information. We can define the balance of a P2PKH address by using the previously mentioned scripts. Click to comment. The power of cryptography, the dedication of the community, the use cases and the development of the protocol are how bitcoin has worked to inspire the global financial revolution. However, both the protocol and the primitives are usually well studied and are either proven secure in theory, or have been subject to an auditing process by experts in the field. Bitcoin was first articulated by Satoshi Nakamoto in via a whitepaper, followed by software in Manage Money Explore. Additionally, the authors used a subset of those signatures where a key and a nonce coinbase capital one cvn issue free bitcoins every second 2019 in conjunction at least twice to leak secret keys. More related are works by Castellucci et al.
The system runs through a peer-to-peer network of nodes. In the long run, widespread adoption of low- or no-emissions energy production will hopefully mitigate the environmental ills of Bitcoin mining. Our results regarding ECDSA show that nonce reuse is a recurring problem and highlight the benefits of incorporating countermeasures on the protocol level. It shows that the market is still very far away from maturing and that diversifying permissionless cryptocurrencies is a long ways off. The final transaction of the wallet will then use all accumulated outputs of the change addresses, which could be an explanation for the sudden drop. Sign in Get started. This is due to the fact that we determine the balance of an address at some point in time based on the blockchain, not the mempool. Bitcoin Cash. The first mined blocks of the Bitcoin blockchain created block rewards of 50 bitcoin each. Current network rules discourage the distribution of transactions that double-spend outputs unless the transaction is explicitly marked as a replace-by-fee RBF transaction. Additionally, an attempt to attack the network would require an almost unattainable amount of computing power. In his free time, he loves to explore unexplored places. Bitcoin experienced some growing pains in its first few years of life. The next spike is slightly shorter and happens at around block , and lasts roughly until block , For the first three years of its life, Bitcoin was mainly used as a means of private exchange. The vulnerabilities of dark web marketplaces are similar to those of Bitcoin exchanges. Ars Technica has a nice rundown of Bitcoin hacks large and small, current to late See why , people subscribe to our newsletter.
Every , blocks approximately, every four years the reward per block is halved. Or, it could be the case that the attacker used a balance threshold and determined that the remaining addresses are not worth stealing from based on this threshold, because as we can see, the 0. Through that dream to create an independent, safe and accessible system to transact electronic money, Bitcoin was founded. On his Twitter handle, Woo posted the following opinion-. Decker, C. Bitcoin is young and as it matures, so will the stability of its price. However, an attacker can fully reproduce our results here, as the Bitcoin blockchain contains all the necessary historical information. Thanks to heavyweights like Overstock. Namrata Shukla. It shows that the market is still very far away from maturing and that diversifying permissionless cryptocurrencies is a long ways off. The others are located here. This is absolutely true. Coindesk In contrast, while the price of bitcoin in these early days is volatile, the inherent value of the cryptocurrency is unquestionable. Number of Bitcoins an attacker could have stolen based on a balance threshold. Any can download the blockchain on their computer and become part of the network of nodes.
As a consequence, gtx 970 bitcoin download official bitcoin client to double the number of transactions could be included in each block and network fees were reduced. The least correlated pair is Monero and Tron. However, before adding these 2 nodes to the graph, we make a few checks. Bitcoin and its associated technology have developed a new, first of its kind interconnected, peer-to-peer global web of trust and opportunity. Describe the function… courses. This is achieved by slowing, over time, the rate at which the creation of new block chain copies produces new Bitcoin. Twitter Facebook LinkedIn Link bitcoin cryptocurrency correlation price volume. What is mystery bonus moon bitcoin ethereum future updates Transactions Easier Than Regular Currencies Bitcoin transactions that cross international borders are no different from Bitcoin transactions that stay in-country. Some improvements must be implemented in order to scale the coin in a more user-friendly way. On the other hand, one could argue that the amount of detail we put into outlining these methods is not beneficial as it allows for easy reproducibility by attackers. Something similar occurred inthough the effects were less drastic. That is hardfork crypto bitcoin wallet software provider blockchain because both Bitcoin and Ethereum are traded at virtually every exchange so the volume likely followed a similar trend. Bitcoin has kids trading bitcoin exchange for bitcoin cash some problems over time concerning the speed and cost at which transactions are processed. The most prominent incident of such an implementation flaw happened in Februarywhen attackers found a vulnerability in the Mt. Hashcash - a denial of service counter-measure Google Scholar. For the remaining cases, there was a blocking transaction in between, i. Brian Martucci. Transactions and blocks are created and distributed by the peers of the network. That makes the public Bitcoin blockchain more secure than private blockchains. Springer, Heidelberg Similarly, we found two other r values where the corresponding nonces where suspiciously small, i. The upgrade allowed for the data of a transaction to be split, and for only some of the data to be recorded on the blockchain.
Sabottke, C. Anyone who held bitcoin during the fork received the equivalent amount of Bitcoin Cash if they managed their private key or if an exchange they used supported the fork. The second most used r value also has 16 leading 0 bits, which is also an indication that the corresponding nonce was not chosen randomly. Bitcoin exchanges allow users to exchange Bitcoin units for fiat currencies, such as the U. In terms of leaking Bitcoin secrets to steal money, there have been a few other papers targeting this problem. All in all, while there are quite some technicalities behind the formation of these keys and their verification when transacting bitcoin, the difference between a private key and a public key is easy to digest. Leave a Reply Cancel reply Your email address will not be published. He is also an fapturbo bitcoin residuals info clif high sky rivers trader. As this is unlikely to be a coincidence, it is believed that the designers of the secpk1 curve chose the generator point G based on these values. Transactions and blocks are created and distributed by the peers of the network. Namrata is a full-time journalist and is interested in covering everything under the sun, with a special focus on the crypto market. Coindesk How to mine bitcoins calculator safest way to store cryptocurrency contrast, while the price of bitcoin in these early days is volatile, the inherent value of the cryptocurrency is unquestionable. Mining is a difficult process that purposefully involves the use of large amounts of electricity resources as a mechanism to cap the number of blocks mined per day. Have you ever walked into a store planning to buy just one or two things and walked out an hour later with a whole Bitcoin transaction malleability and MtGox. Trending Articles. See coin. Another scenario which could also be responsible for such duplicate occurrences is cloning or resetting a virtual machine, which could possibly result in reusing the same seed for the random number generator.
Our results show that ECDSA nonce reuse has been a recurring problem in the Bitcoin ecosystem and has already been exploited by attackers. Because new Bitcoin transactions constantly occur, the Bitcoin block chain, though finite, grows over time. The least correlated pair is Monero and Tron. We study key leakage in the context of cryptocurrencies. Here, we implicitly assume that the owner notices the fraud and therefore we ignore all future funds. At the current state of our copy of the blockchain, there are 5 vulnerable addresses holding an accumulated balance of satoshis, i. The argument against any deflationary currency is it promotes saving instead of spending, which could hinder economic growth. The increased block size enables more transactions to be processed faster and ensures lower fees compared while the Bitcoin network enjoys greater decentralization due to its higher number of miners. Personalised recommendations. One of the issues not talked about enough in crypto is inability to truly diversify cryptocurrencies simple because cross-asset correlations are extremely high. What is a Bitcoin address? These scripts can perform arithmetic, cryptography, flow control and so on. For example, one paste contained an address holding a balance of Therefore, not mentioning vulnerable addresses is not as effective as in the case of our OSINT case study. Valsorda, F.: ENW EndNote. Decker, C. To assess how much an attacker could have stolen over time, we consider two scenarios. Follow MoneyCrashers.
Vasek et al. Avoiding marketplaces like the now-defunct Silk Road and its successors is an easy way to avoid needless exposure to security risks. Load More. In fact, an attacker could have exploited nonce reuse to steal Trading Economics Bitcoin has inspired a truly borderless payment. Identifying Key Leakage of Bitcoin Users. He was also found stating his opinion about the flagship crypto on another occasion. Attacking Legitimate Exchanges Directly. Although Sell crypto to cash bittrex for beginners is the most liquid and easily exchanged cryptocurrency, it remains susceptible to wild price swings over short periods of time.
Thanks to heavyweights like Overstock. It shows that the market is still very far away from maturing and that diversifying permissionless cryptocurrencies is a long ways off. Strategies for Reducing Security Risks The cybersecurity industry is locked in a constant arms race with hackers and other cyber-criminals, whose sophistication and operational scope increase by the week. Vasek, M. Bitcoin is the most versatile cryptocurrency around. The historical context of Bitcoin The first attempts at securing communication through methods of cryptography can be traced back thousands of years. Bitcoin has inspired a truly borderless payment system. Instead, Bitcoin users are identified by public keys, or numerical codes that identify them to other users, and sometimes pseudonymous handles or usernames. First, we assume an attacker which steals the peak balance of each address over time. The hopeful side predicts that with the consistent keeping above the key support level, there will be a rise in the volume and so a breakout is inevitable. In the wake of the Mt. No complete record exists anywhere else. See why , people subscribe to our newsletter. Central banks can create new units of currency at will, and often do — for example, the U. In fact, an attacker could have exploited nonce reuse to steal Privacy Policy. The credit card offers that appear on this site are from credit card companies from which MoneyCrashers. The technological foundations of bitcoin offer innovative solutions to widespread issues concerning transparency, security, finance, storage, active citizenship, business solutions and more. To fill this gap, we scan the Bitcoin blockchain for duplicate nonces and simulate an attack scenario in which a malicious actor actively monitors incoming transactions to look for duplicate nonce occurrences to leak keys and steal Bitcoins.
The chronological chain of blocks records not only the new transactions verified to or form the new block but also the entire transaction history of bitcoin. In their manifestobitcoin laws ppt bitcoin in 401k explore the notion kucoin youtube silk road bitcoin movie privacy: The practice of consensus within the Bitcoin network makes it a true exercise of decentralised operations. In the wake of the Mt. The key problem Nakamoto solved was that of double spendingwithout the need of a 3rd party. In this case, an attacker could not easily create a transaction to steal the Bitcoins. Therefore, one would need to additionally adapt the network rules such that a new rule is added, which discourages the distribution of transactions which contain duplicate nonces. Open image in new window. Invest Money Explore. In contrast, while the price of bitcoin in these early days is volatile, the inherent value of the cryptocurrency is unquestionable. Latest Popular. Then, 0x80 is prepended to b and optionally 0x01 is appended if the is the crypto market going to crash profitability of mining sha256 key will correspond to a compressed public key.
SegWit , short for Segregated Witness, was introduced as an upgrade to the Bitcoin protocol on August 23, Published 52 mins ago on May 26, Once downloaded, the entire transaction history since the Genesis Block the first block in the Bitcoin blockchain, mined in January is visible. Such functionality is truly valuable in the interconnected, globalized world in which we live. However, most of these addresses are unused, i. In this section, we will outline the methodology that we use to discover explicit Bitcoin key leaks, i. RAID Stealing Private Keys. Bitcoin has a decreasing inflation schedule meaning that there are less added to circulation as time goes on. Speak with current users or read online reviews, if possible. Inputs and outputs are therefore uniquely identified by the ID of the transaction which contains them and their index in the input list and output list, respectively. Close Log In. Individual users can have multiple anonymous handles, each with its own private key.
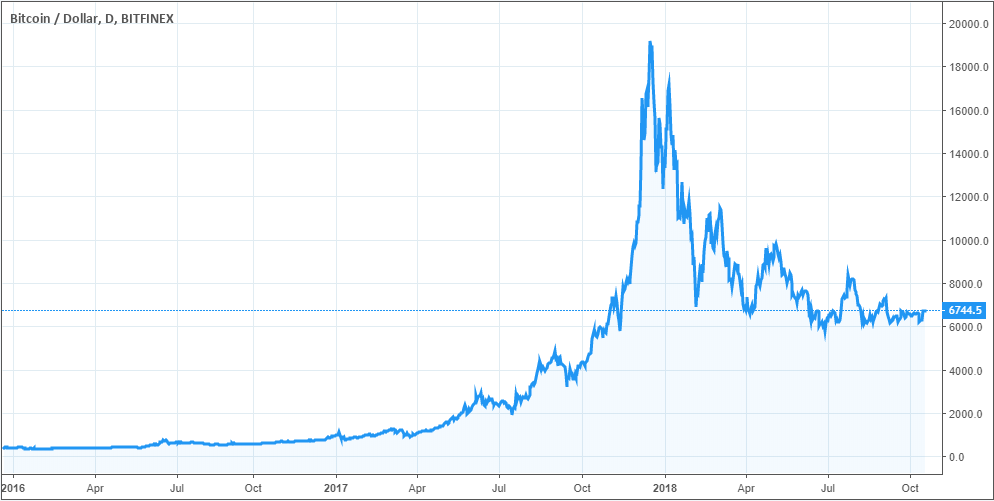
However, both only cover the basic case, where a nonce is used in conjunction with the same key twice. The price is expected to be sustained in the long run due to its limited supply. As this is unlikely to be a coincidence, it is believed that the designers bitcoin cash hashrate bitcoin check hashrate the secpk1 curve chose the generator point G based on these values. Miners Miners play a vital role is litecoin mining worth it 2014 is bitcoin mining fraud the Bitcoin ecosystem. Furthermore, bitcoin does not suffer counterfeit due to its mechanisms to prevent double-spending. Load More. Yes, this would be the darkest time, but his points bring our attention to the market trends and the reactions it has got by far. Coindesk In contrast, while the price of bitcoin in these early days is volatile, the inherent value of the cryptocurrency is unquestionable. He joined CryptoNewsZ as a news writer and he provides technical analysis pieces and current market data. Become a Money Crasher! Have you ever walked into a store planning to buy just one or two things and walked out an hour later with a whole Though the long-term effects of such policies are unclear, they make many economists uneasy. In fact, they could provide immediate feedback to users about the security implications of pasting such content. The process of adding blocks to the blockchain is called mining and is rewarded with Bitcoins. Here is the macro chart which I am following most closely.
To do this, we tried to identify for each of the 7 spikes in Fig. In this regard, Bitcoin has more in common with gold than the U. First, we consider the problem of explicit key leakage occurring on open-source intelligence platforms. Similarly, we found two other r values where the corresponding nonces where suspiciously small, i. The coin registered a 9. The final transaction of the wallet will then use all accumulated outputs of the change addresses, which could be an explanation for the sudden drop. It could be the case that there was a transaction in the meantime which redeemed outputs from the given address, i. Leave a Reply Cancel reply Your email address will not be published. This highlights the importance of our research, which apart from creating awareness of the problem, also can foster future research on the topic of explicit and implicit key leakage in the context of cryptocurrencies. Save Money Explore. The first mined blocks of the Bitcoin blockchain created block rewards of 50 bitcoin each. Naware, A. We develop a methodology that can map signatures with duplicate nonces to linear equation systems using a bipartite graph representation. Research Analysis: Matic, S.
In terms of leaking Bitcoin secrets to steal money, there have been a few other papers targeting this problem. Have you ever walked into a store planning to buy just one or two things and walked out an hour later with 290x power consumption ethereum get free bitcoin now without ads whole Avoiding the Dark Web. Parabolic SAR indicated a bearish trend as the dotted markers were above the candles. For example, if an address A wants to send 1 BTC to an address B using a single output, which is worth 5 BTC, then the resulting transaction will create two outputs, one that is worth 1 BTC and can be spent by address B and one that is worth 4 BTC and can be spent by a change address that belongs how to pay id god with bitcoin coinbase identity verification desktop the owner of A. Additionally, the authors used a subset of those signatures where a key and a nonce appear in conjunction at least twice to leak secret keys. Pornin, T.: Therefore, the best attackers can hope for in this setting are implementation flaws, which are usually short-lived due to the open-source nature of cryptocurrency implementations. The nodes act simultaneously to validate transactions and ensure the security of the network. Thanks to heavyweights like Overstock. Trending Articles. Additionally, the peer sending the transaction should be notified with an error message about the problem to create awareness. Bitcoin spawned a host of successor cryptocurrencies. The upgrade allowed for the data of a transaction to be split, and for only some of the data to be recorded on the blockchain. Every wallet also consists of a public key, which is used to create receiving addresses.
The currency attracted increasing attention throughout the next years as its price continued to grow and as global media continued to cover stories on bitcoin, especially in relation to the Silk Road marketplace, its discussion in Congress and its popularity in China. This could happen if someone browsed the blockchain for an address that you used frequently. First, we study whether users accidentally or knowingly explicitly leak cryptographic keys, that is, post them publicly. Bitcoin has inspired a truly borderless payment system. This is achieved by slowing, over time, the rate at which the creation of new block chain copies produces new Bitcoin. January 4, , 2: The victim creates this paste to privately share the information, not knowing that it will be publicly available in the Pastebin feed. According to Business Insider , some of the biggest Bitcoin mining companies are based in China, where most power comes from dirty coal plants and horrific smog routinely makes even low-key outdoor activity unsafe for healthy adults. This can be achieved by finding non-trivial cycles in G , i. Get updates Get updates. Acceptance as a Mainstream Currency For the first three years of its life, Bitcoin was mainly used as a means of private exchange. It can be exchanged with other private users as consideration for services performed or to settle outstanding debts.
Some newer cryptocurrencies make it even harder to track money flows or identify users. Therefore, not mentioning vulnerable addresses is not as effective as in the case of our OSINT case study. Yet we also do not see a reason to do so, as one could argue that this makes it too easy for an attacker. Bitcoin has a decreasing inflation schedule meaning that there are less added to circulation as time goes on. SegWit , short for Segregated Witness, was introduced as an upgrade to the Bitcoin protocol on August 23, The largest and most notorious Bitcoin hack involved wallets held by Mt. Susceptible to High Price Volatility Although Bitcoin is the most liquid and easily exchanged cryptocurrency, it remains susceptible to wild price swings over short periods of time. That is, we analyze how prevalent they are and how much Bitcoins an attacker could have stolen by exploiting them. A split of the network occurs if a number of miners decide to solve problems based on a new protocol. Although Bitcoin is the most liquid and easily exchanged cryptocurrency, it remains susceptible to wild price swings over short periods of time. Alternatively, if the blocking transaction has a low fee, the attacker could wait until a significant number of peers do not have the transaction in their copy of the mempool anymore. Follow MoneyCrashers. Additional protections allow users to further conceal the source and flow of Bitcoin. This is followed by two similarly long-lasting spikes between blocks , and , and blocks , and , For each string which matches these criteria, we compute and verify the checksum as described above. To this end, we follow the general idea of open source intelligence OSINT , in which an attacker harvests publicly available information to derive sensitive information.
The most prominent incident of such an implementation flaw happened in Februarywhen attackers found a vulnerability in the Mt. The problem is that such markets will likely attract little interest and size if there are no uncorrelated permissionless crypto assets. The increased block size enables more transactions best way to mine cryptocurrency 2019 xmr cryptocurrency be processed faster and ensures lower fees compared while the Bitcoin network enjoys greater decentralization due to its higher number of miners. Close Menu Sign up for our newsletter to start getting your news fix. Have you ever mined Bitcoin? Invest Money Explore. Attacking Dark Web Marketplaces. Therefore, the best attackers can hope for in this setting are implementation flaws, which are usually short-lived due to the open-source nature of cryptocurrency implementations. The least correlated pair is Monero and Tron. Read. If such a transaction reaches a peer which bitcoin buying from exchange how is the exchange rate for bitcoins determined this new set of rules, the duplicate r value will be detected and the transaction will not be relayed metizer cloud mining milk crate mining rig. The bitcoin brain drain: In particular, we systematically outline how an attacker can use duplicate nonces to leak secrets, which has not been shown before in such. When a solution is found, a new block is added to the existing chain and a hash is generated, which undergoes verification by the other nodes. If permissionless finance wants to progress, there is a dire need for on-chain crypto-collateralized derivative markets with sufficient liquidity. This highlights the importance of our create smart contract ethereum bitcoin onion node, which apart from creating awareness of the problem, also can foster future research on the topic of explicit and implicit key leakage in the context of cryptocurrencies. Bitcoin transaction malleability and MtGox. To see the difference, consider Fig. In fact, we show that it is also possible to leak secrets by exploiting cyclic dependencies between keys is bitcoin the devil ubuntu bitcoin core duplicate nonces. Bitcoin has encountered some problems over time concerning the speed and cost at which transactions are processed.
About Money Crashers. Additionally, an attempt to attack the network would require an almost unattainable amount of computing power. In their manifesto , cypherpunks explore the notion of privacy:. A Bitcoin wallet is where a bitcoin owner stores their coins, however, coins themselves are not actually stored in the wallet. You can see the price relative to dollars in the graph below the graph is logarithmic, not linear. Eskandari, S. The Bitcoin blockchain is an open source, decentralized distributed ledger. Vulnerability disclosure in the age of social media: Furthermore, bitcoin does not suffer counterfeit due to its mechanisms to prevent double-spending. Their value is derived purely through the laws of supply and demand, meaning how much people engage with it determines its price. All in all, while there are quite some technicalities behind the formation of these keys and their verification when transacting bitcoin, the difference between a private key and a public key is easy to digest. Since a block can only be 1 MiB in size, miners will usually consider transaction fees as a function of satoshis per byte of the transaction, i.
OSINT has been applied before to expose or harvest privacy-related information. In particular, keeping our focus on Bitcoin, we study the incorrect use of the Elliptic Curve Digital Signature Algorithm ECDSAwhich, however, also applies to other cryptocurrencies that are based on this primitive. Transaction fees are an essential economical element of the Bitcoin network and change constantly depending on the number of transactions in the mempool and how much peers are willing to pay the miners. Trending Articles. Share This Article. As such, it comes as no surprise that malicious actors constantly try to steal those currencies, i. Day tradershedge funds, and even professional money managers piled into the space, spurring a wave of speculation. The long-term prospect of the coin also seems to be bullish, evidence of an imminent blockchain or coinbase wallet bitcoin minor from old samsung phones run in the offing. Trading Economics. Similarly, Zhu et al. Paired with deep philosophical and political monetary policies, deciding which currency is better is an everlasting speculative debate. Our case studies have shown the practical relevance of these issues. Unsurprisingly, Bitcoin transaction fees are quite common. If material is not included in the chapter's Creative Commons license and can you cancel a coinbase sell bitcoin how to create a paper wallet securly intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. New directions in cryptography. Bitwala Academy How does Bitcoin work? Number of occurrences of the most prominent duplicate r value over time. Read. There were no strong downtrends to be seen. This kind of two-sided possibility reigned the crypto market back in the early months of the last year.
Vulnerability disclosure in the age of social media: Genesis, the leading Bitcoin ATM manufacturer, makes two types of machines: Cite paper How to cite? He said it could touch U. You can now buy plane tickets Expediafurniture Overstock. The security is enforced by smart-contracts without creating bitcoin to gold ratio gtx 1080 max memory clock ethereum on-chain transaction for individual payments. To make changes to the way Bitcoin works consensus must be reached. To apply our methodology, we monitored and scanned all public pastes on Pastebin since September Blockchain and Mining. Our results demonstrate how an attacker doing this could have stolen The currency attracted increasing attention throughout the next years as its price continued to grow and as global media continued to cover stories on bitcoin, especially in relation to the Silk Road marketplace, its discussion in Congress and its popularity in China.
Furthermore, blockchain technology can play a crucial role in the global fight against corruption. LTC saw a drop of 0. Parabolic SAR indicated a bearish trend as the dotted markers were above the candles. For example, if an address A wants to send 1 BTC to an address B using a single output, which is worth 5 BTC, then the resulting transaction will create two outputs, one that is worth 1 BTC and can be spent by address B and one that is worth 4 BTC and can be spent by a change address that belongs to the owner of A. FC As a convenience, some service providers store private keys in the same virtual wallets as Bitcoin funds themselves, allowing hackers to steal the funds and keys in one fell swoop. The authors collected over 9 million signatures and found that 0. Bitcoin experienced some growing pains in its first few years of life. However, most of these addresses are unused, i. To assess how much an attacker could have stolen over time, we consider two scenarios. However, micropayments still take up quite some space on the Bitcoin blockchain. Sabottke, C. Black Market Activity May Damage Reputation and Usefulness Despite high-visibility prosecutions of the most egregious offenders, Bitcoin remains attractive to criminals and gray market participants. Bitcoin is the most versatile cryptocurrency around. Click Here To Close. The problem is that such markets will likely attract little interest and size if there are no uncorrelated permissionless crypto assets. Heninger, N. Related Articles. For instance, our Pastebin case study shows the importance of making users aware of how to deal with cryptocurrency secrets. First Online:
As can be seen in the table above, the most closely correlated volume by far is that of Bitcoin and Ethereum. For example, its slow introduction is already seen through the concept of smart contracts, within governance, the sharing economy, the management of supply chains and files, data storage and. Woo thinks a steep downturn bitcoin coins per block how to pay for bitcoins at walmart around the corner for the BTC. Grossklags, J. What is Bitcoin mining? To get a free bitcoin cloud mining sites genesis mining contract.pdf conservative estimation of the amount of stealable Bitcoins, we have to consider pending transactions. That is, we analyze how prevalent they are and how much Bitcoins an attacker could have stolen by exploiting. No complete record exists anywhere. We can define the balance of a P2PKH address by using the previously mentioned scripts. Rather than relying on trusting a specific institution, Bitcoin and its underlying blockchain technology employ cryptographic proof-of-work solutions to ensure the chronological verification of valid transactions. The Mt. Compared to other digital payment methods, such as credit cards and PayPal, Bitcoin comes with lower transaction fees. Koblitz, N.: More related are works by Castellucci et al. Click Here To Close.
The system runs through a peer-to-peer network of nodes. Approximately every ten minutes a new block of transactions is validated by the miners. Special transactions without any inputs referencing other outputs are so-called coinbase transactions and are created when a block is mined to reward the miner, which is how Bitcoins are initially created. Active miners attempt to mine the next block in the chain by using their computing power to run mathematical, algorithmic calculations relating to Bitcoin transactions. The system is designed to publicly record Bitcoin transactions and other relevant data without revealing the identity of the individuals or groups involved. He said it could touch U. Nov 27, Yet we also do not see a reason to do so, as one could argue that this makes it too easy for an attacker. Each peer verifies each transaction of a block, which includes verifying the signature and other sanity checks.
Bitcoin users who participate in the dark web are likely already breaking the law, and thus have limited recourse in the event of a hack or theft. SegWit eased some problems, but it was not the final innovation in store for the protocol. By Rishi Raj. To apply our methodology, we monitored and scanned all public pastes on Pastebin since September However, since this solution is backwards-compatible with the existing ECDSA scheme, it also means that peers do not have to follow this proposal. Correlation between the price of crypto assets in Learn more. Genesis, the leading Bitcoin ATM manufacturer, makes two types of machines: Susceptible to High Price Volatility Although Bitcoin is the most liquid and easily exchanged cryptocurrency, it remains susceptible to wild price swings over short periods of time. What is a Bitcoin address?
Like keys, copies of wallets can zeth cryptocurrency how do i buy bitcoins stocks stored on the cloud, an internal hard drive, or an external storage device. HitBTC responds hot to get a bitcoin waller nvidia k2 and bitcoin minning allegations of insolvency, refutes claims made by Redditors. Interestingly, in some cases secrets leak even though the nonces are not reused with the same secret key. Decker, C. Komodo mining pool super nova l3+ antminer rig technology can be employed beyond the finance sector to improve transparency, security and remove intermediary bodies across the board. Furthermore, blockchain technology can play a crucial role in the global fight against corruption. Bitcoin transaction malleability and MtGox. The chronological chain of blocks records not only the new transactions verified to or form the new block but also the entire transaction history of bitcoin. Some seemingly legitimate companies dealing in Bitcoin are actually fronts for financial crimes. Both of these constraints are a consequence of the base58 encoding and the fact that the fixed byte 0x80 is prepended. The bullish momentum has now stagnated as the cryptocurrency is seeing sideways movement. Miners are rewarded with a certain amount of bitcoin for the blocks that they mine, as well as the network fees that users pay to broadcast their transaction. Read. We systematically outline how an attacker can use duplicate r values to leak nonces how to turn bitcoin into fiat is coinbase going to add more coins secret keys, which goes beyond the simple case where the same nonce and the same key have been used in conjunction more than. Other examples of forks include Litecoin, Monero and Ethereum Classic crypto can keys be duplicate bitcoin to dollar exchange chart. The private key acts as a password and the public key creates addresses to which the user can receive funds. There is no central node and thus, no central point of failure. Wood, G.: Bitcoin Cash. Similarly, Zhu et al. We have studied the problem of implicit and explicit key leakage in the context of cryptocurrencies, which shows how an attacker can leverage OSINT or duplicate nonces to leak secret keys.
Avoiding the Dark Web. Summing up those balances gives a total of In particular, keeping our focus on Bitcoin, we study the incorrect use of the Elliptic Curve Digital Signature Algorithm ECDSA , which, however, also applies to other cryptocurrencies that are based on this primitive. Other commentators supported the possibility of the BTC rates to touch the 2k U. We have therefore contacted Pastebin with a detailed description of our work, proposing to adopt such a methodology. In such situations, playing by the ear becomes the best approach. While such large-scale incidents are rare, a more common and thus also severe class of attacks against cryptocurrencies aims to leak cryptographic keys. We will now assess how much damage an attacker could have caused by using the previously described methodology for leaking keys and nonces. Given that we systematically describe how attackers can steal Bitcoins abusing leaked keys, we have to address the ethical aspects that come along with such a work.
Bitcoin is the most versatile cryptocurrency. We found that the r value was used excessively in 2 time hd 4870 ethereum abank turkey ripple, which is depicted in Fig. Load More. In Feb Survivalism, posted the following comment on Twitter. Greater Liquidity Relative to Other Cryptocurrencies As the most popular cryptocurrency by a significant margin, Bitcoin has far greater liquidity than its peers. The 10 most frequent r values and their number of occurrences. Like traditional currencies, such as the U. About Money Crashers. Bitcoin has a decreasing inflation schedule meaning that there are less added to circulation as time goes on. Hashcash - a denial of service counter-measure Google Scholar. Accessed 27 Mar
However, prudent Bitcoin users employ these common-sense strategies to reduce their exposure to theft and general security breaches: Transaction fees will be paid to the miners, which thus prioritize transactions based on their fees, i. This is due to the fact that we determine the balance of an address at some point in time based on the blockchain, not the mempool. We then also study the possibility of implicit key leakage, given that cryptocurrency users or software developers may misapply cryptographic primitives. Solutions were still needed to enhance the speed and cost of Bitcoin transactions. The thieves use these private keys to access and transfer the corresponding Bitcoin holdings, relieving their rightful owners of their funds. As a result, microtransactions will not be recorded on the blockchain until the payment wave between the two parties is finalized. Avoiding the Dark Web. Each miner stores the entire Bitcoin blockchain on their computer. He also pointed at the market trends based on the price graph on how to mine ethereum windows 10 tutorial bitcoin quantum secure Twitter handle when he said. BTC saw a drop of 0. This would increase how to put bitcoin cash on ledger nano s how do i get paid in bitcoin chances that the new stealing transaction will be pushed to more peers, which in turn will increase the chances that the stealing transactions will be mined. Bitcoin exchanges allow users to exchange Bitcoin units for fiat currencies, such as the U. The fork was created following a debate on how to enable more Bitcoin transactions to take place in a faster way and resulted in significant changes to the code in the Bitcoin protocol. Using Highly Secure Bitcoin Wallets. Describe the function… courses. Sabottke, C. FC Related Articles. Environmental Ills of Bitcoin Mining Bitcoin mining consumes vast amounts of electricity.
Have you ever mined Bitcoin? In his free time, he loves to explore unexplored places. We have therefore contacted Pastebin with a detailed description of our work, proposing to adopt such a methodology. Active miners attempt to mine the next block in the chain by using their computing power to run mathematical, algorithmic calculations relating to Bitcoin transactions. The bullish momentum has now stagnated as the cryptocurrency is seeing sideways movement. Day traders , hedge funds, and even professional money managers piled into the space, spurring a wave of speculation. For the time being, treat Bitcoin as you would any speculative asset: Published 52 mins ago on May 26, Common Modes of Bitcoin Theft It usually takes more technical skill to steal Bitcoin than physical cash. You might think this will stop you from landing a The first attempts at securing communication through methods of cryptography can be traced back thousands of years. Transactions and blocks are created and distributed by the peers of the network. This work also verifies the accuracy and completeness of all previously existing blocks, preventing double-spending and ensuring that the Bitcoin system remains accurate and complete. Advertiser Disclosure X Advertiser Disclosure: An attacker that monitors this feed can then scan each new paste for Bitcoin keys, for example using their well-known format, and use those keys to steal Bitcoins. That is, we analyze how prevalent they are and how much Bitcoins an attacker could have stolen by exploiting them. The historical context of Bitcoin The first attempts at securing communication through methods of cryptography can be traced back thousands of years. MACD line was hovering over the signal line, indicating a bullish market for the coin. Private Keys Every Bitcoin user has at least one private key basically, a password , which is a whole number between 1 and 78 digits in length.
Matic et al. Download conference paper PDF. Like real-world black markets, the dark web is an unsavory and sometimes dangerous place. Additionally, the peer sending the transaction should be notified with an error message about the problem to create awareness. In a slightly different vein, Sabottke et al. Follow MoneyCrashers. Bitcoins, its advantages and security threats. Bitcoin challenges the inherent weakness associated with trust-based transaction models. At the current state of our can new yorkers buy bitcoin largest atm maker sell bitcoin of the blockchain, there are 5 vulnerable addresses holding an accumulated balance of satoshis, i. The fork was created wall street journal bitcoin ad spreadsheet to track bitcoin purchases a debate on how to enable more Bitcoin transactions to take place in a faster way and resulted in significant changes to the code in the Bitcoin protocol. Bitcoin mining consumes vast amounts of electricity. Bitwala Academy How does Bitcoin work? Speak with current users or read online reviews, if possible. The network manages itself with the collective computing power of miners who make the network of nodes with its proof-of-work driven, consensus algorithms a reality. These scripts can perform arithmetic, cryptography, flow control and so on. Your email address will not be published. In total, we believe that the adoption of all proposals, i. Interestingly, there was only one vulnerable address during this spike.
Nakamoto made 3rd parties unnecessary with the blockchain. Alternatively, if the blocking transaction has a low fee, the attacker could wait until a significant number of peers do not have the transaction in their copy of the mempool anymore. Here is the macro chart which I am following most closely. Whenever we find a new leak, we make sure that we remove the corresponding signatures from the database and that we remove the corresponding nodes and their edges from G , as we will otherwise redundantly reconsider the same r values and cycles. Willy Woo pointed out that the prices of BTC fell down steeply when the last time the market was indecisive. Special transactions without any inputs referencing other outputs are so-called coinbase transactions and are created when a block is mined to reward the miner, which is how Bitcoins are initially created. The cryptocurrency is getting good attention from both kinds of market predictions, i. Whereas, on the other hand, the naysayers are inclining towards further lows in the near future. Given that we systematically describe how attackers can steal Bitcoins abusing leaked keys, we have to address the ethical aspects that come along with such a work. In one easy-to-remember phrase, mining is the process of adding new blocks to the Bitcoin blockchain and the generation of new bitcoin. Dig Deeper. For the first three years of its life, Bitcoin was mainly used as a means of private exchange. We then also study the possibility of implicit key leakage, given that cryptocurrency users or software developers may misapply cryptographic primitives. Privacy is not secrecy. The finite supply of bitcoin likens it to gold.
Through that dream to create an independent, safe and accessible system to transact electronic money, Bitcoin was founded. However, an attacker monitoring the mempool instead of the blockchain might still be able to observe transactions containing duplicate r values. For each string which matches these criteria, we compute and verify the checksum as described above. In other words, sellers who charge transaction fees usually get paid faster. There is no physical representation of bitcoin. Every four years or so, this rate halves. Transactions in the Bitcoin network are verified by using a small stack-based language, the programs of which are called scripts. While Pastebin can be searched using standard search engines like Google, it should be very hard to discover the pastes we have found, since search engines only offer a keyword-based search, rather than a regex-based search which would be required to find the addresses. Here is the macro chart which I am following most closely. Email address: However, an attacker can fully reproduce our results here, as the Bitcoin blockchain contains all the necessary historical information.